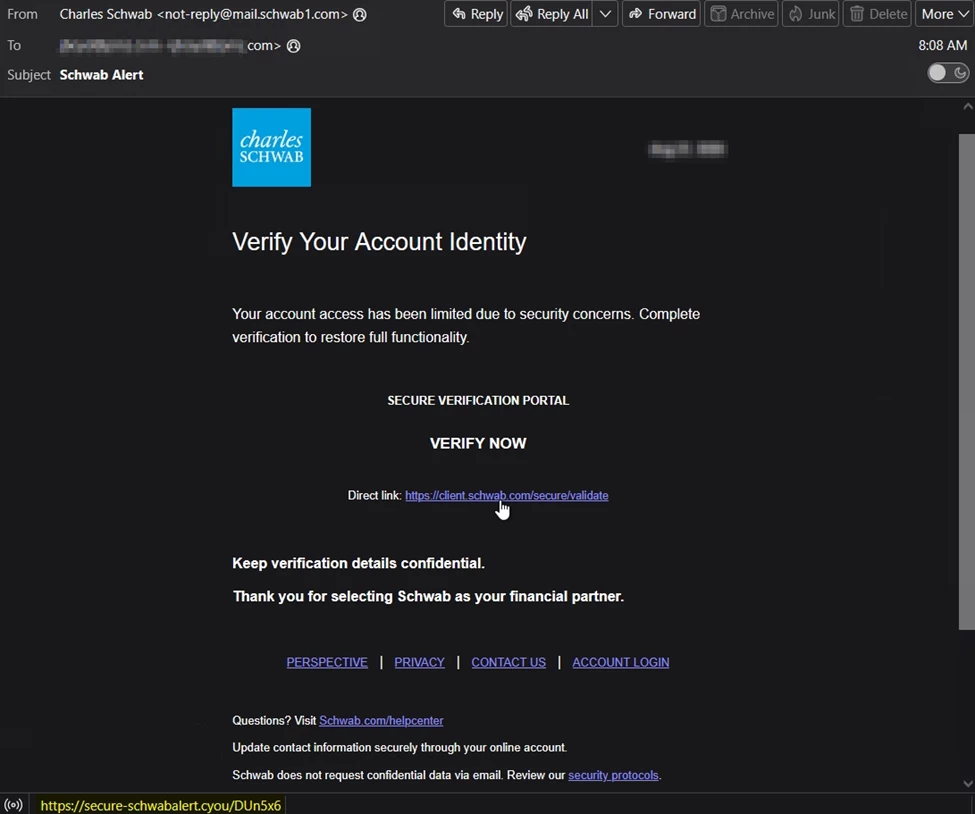
Brokerage and financial firms continue to be prime targets for cybercriminals, as compromised access to investment accounts can quickly translate into financial gain. Over the past several weeks, we have observed a rise in phishing campaigns spoofing Charles Schwab, with messages crafted to create a sense of urgency. In one case, recipients were told that their accounts had been restricted due to security concerns and were urged to verify their identity immediately. While the email displayed a convincing Schwab logo and familiar branding, the embedded link redirected users to a domain registered under the [.]cyou gTLD — a space frequently exploited by threat actors due to its low cost and weak oversight.
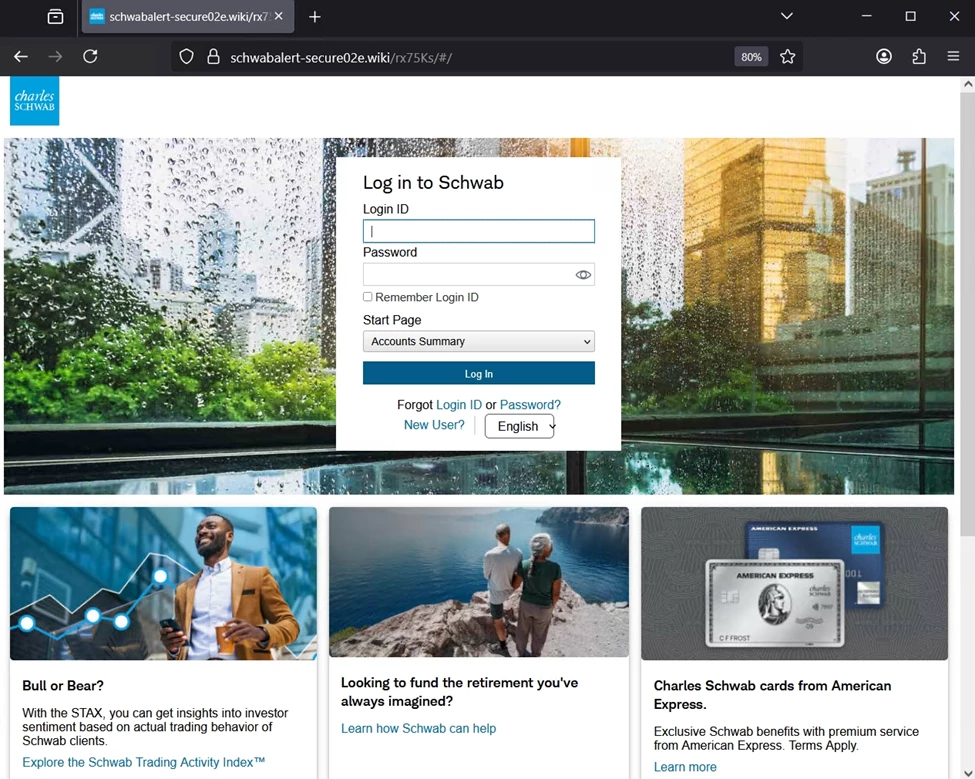
Those who clicked were sent to a fraudulent site designed to mimic the legitimate Charles Schwab login portal, this time hosted on a [.]wiki domain. The cloned page replicated Schwab’s branding and login layout with striking accuracy, leaving little visual indication that users were entering their credentials into a malicious site. This combination of brand impersonation, domain manipulation, and urgency cues makes the campaign particularly dangerous for unsuspecting recipients.
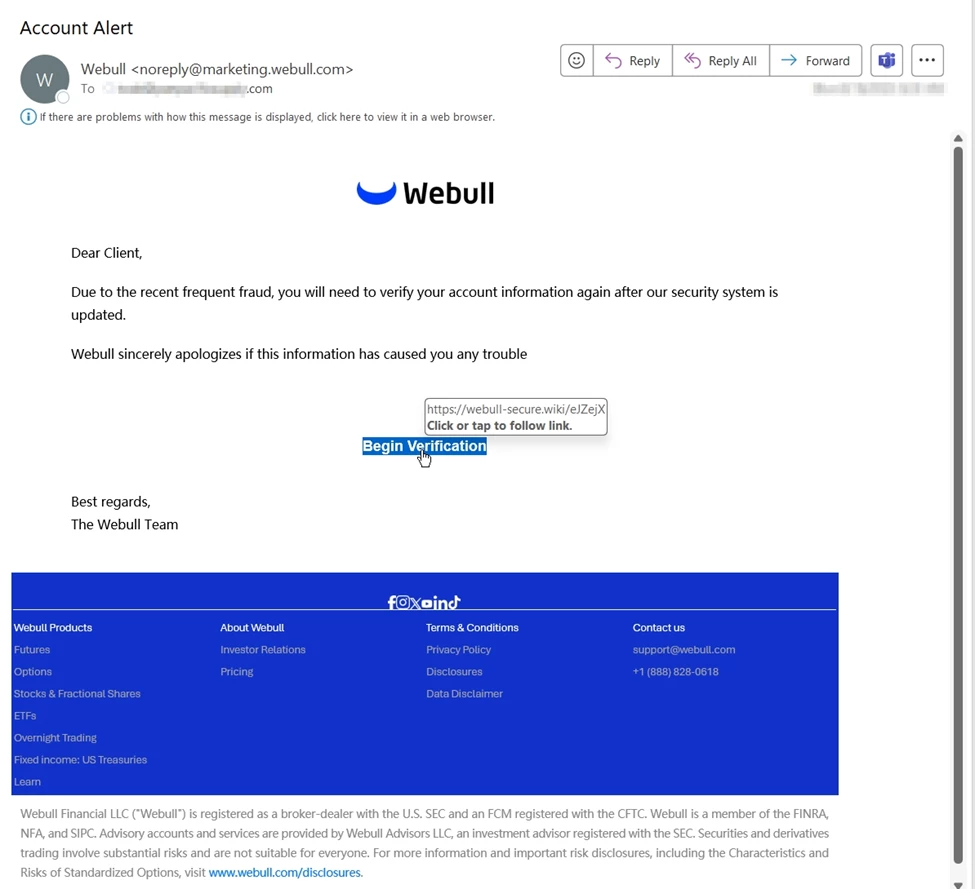
Another campaign, likely connected to the same operators, set its sights on Webull customers. These phishing emails followed a similar pattern, using sender addresses and lures that appeared legitimate, but linking to domains crafted with a company-secure[.]gTLD naming convention. Just as with the Schwab campaign, the attackers deliberately shifted between gTLDs to evade basic filtering. In this case, the email’s malicious link pointed to a [.]wiki domain, where victims were prompted to re-verify their account information.
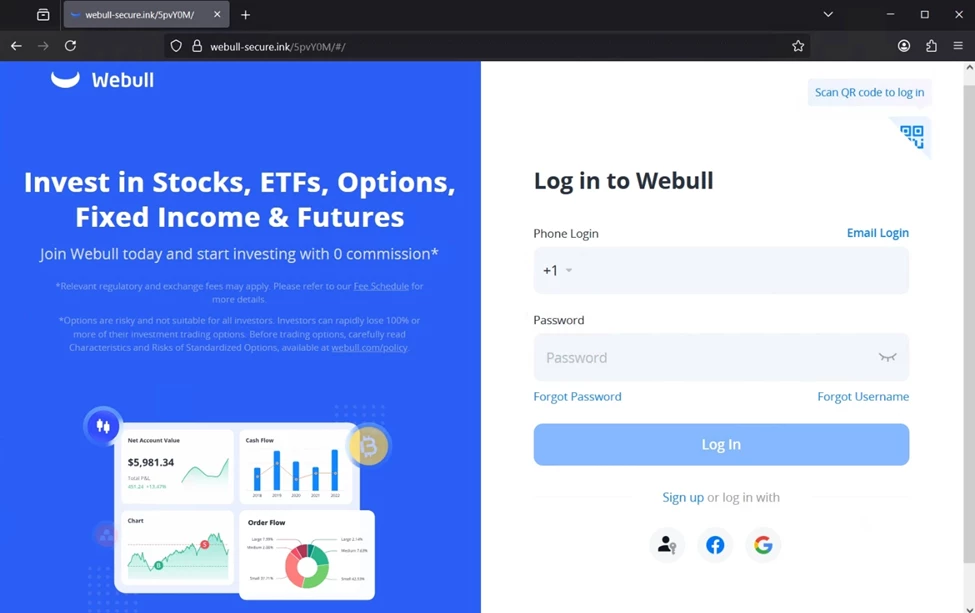
The redirect led to a fraudulent Webull login page hosted on a [.]ink domain. Beyond the surface-level imitation of the Webull platform, the attackers employed the same technical tricks as in the Schwab campaign: JavaScript obfuscation, mirrored file paths, and reused CSS assets. The overlap in tactics and infrastructure strongly suggests that both operations were carried out by the same group, leveraging a shared codebase to scale their credential-harvesting schemes across multiple financial brands.
For individuals and organizations alike, these campaigns underscore the importance of vigilance when handling unsolicited messages related to financial accounts. Users should be cautious of emails that frame account access as restricted or require immediate verification, especially when paired with links that do not clearly belong to the legitimate company’s domain. Hovering over links before clicking can help reveal mismatched or suspicious URLs, while accessing accounts directly through known, bookmarked sites removes the risk of being funneled to a fake login page. Financial firms, meanwhile, can help protect their customers by continuing to educate them about phishing tactics and maintaining clear communication channels for reporting suspicious activity. Although these attacks are growing more polished in their execution, simple awareness and careful habits remain powerful defenses against credential theft.




