On January 4, the Phorpiex botnet, also known as Trik, resumed large scale distribution activity. To date, approximately 3.15 million malicious messages have been captured in association with this campaign, many of which resulted in ransomware deployment within minutes of user interaction. The activity strongly mirrors historical Phorpiex operations, reusing known sender infrastructure and familiar lure patterns. The emails rely on extremely minimal message content and generic urgency, favoring filter evasion over social engineering depth.
The ransomware affiliate tied to this activity appears linked to the LockBit ecosystem and is now operating under the rebranded name Global Group. Emails in this campaign contain a small ZIP attachment designed to resemble a routine document delivery. The attachment naming is intentionally bland, such as “Document.zip,” and the sender identity impersonates a generic support contact to blend into normal business correspondence. Rather than a legitimate file, the archive contains a Windows shortcut that executes an embedded PowerShell command, which retrieves and launches a secondary payload from remote infrastructure with little visible user interaction.
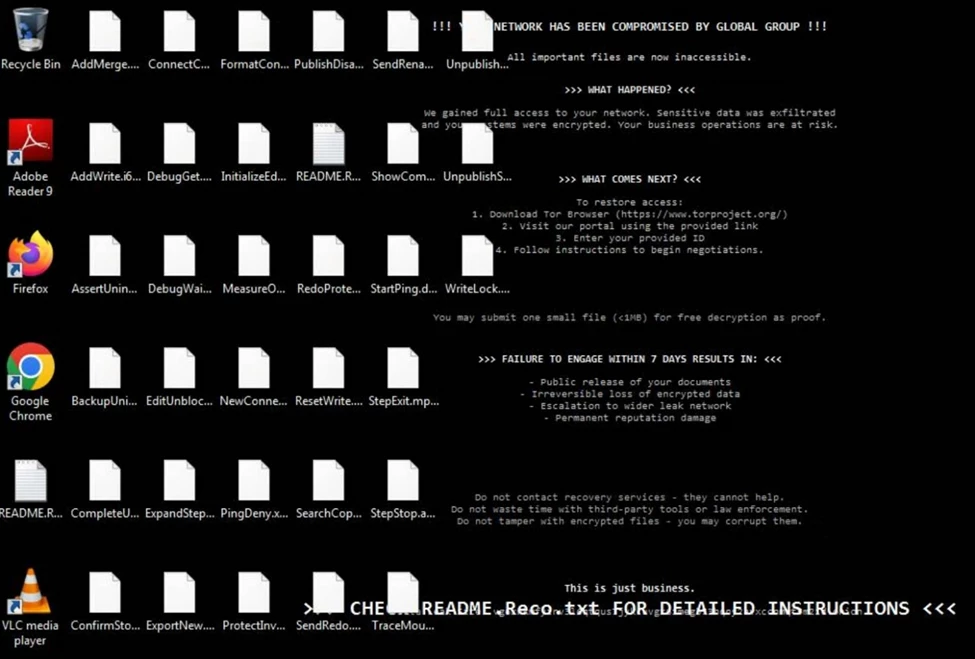
Once executed, encryption begins within minutes and rapidly impacts accessible files across the system. Screenshots show encrypted files spanning both user data and application-related directories, suggesting minimal directory exclusion beyond what is required to keep the operating system functional. Following encryption, the desktop wallpaper is replaced with a compromise notification asserting both data encryption and theft. This messaging reinforces a double extortion narrative despite no immediate on-screen proof of exfiltration.
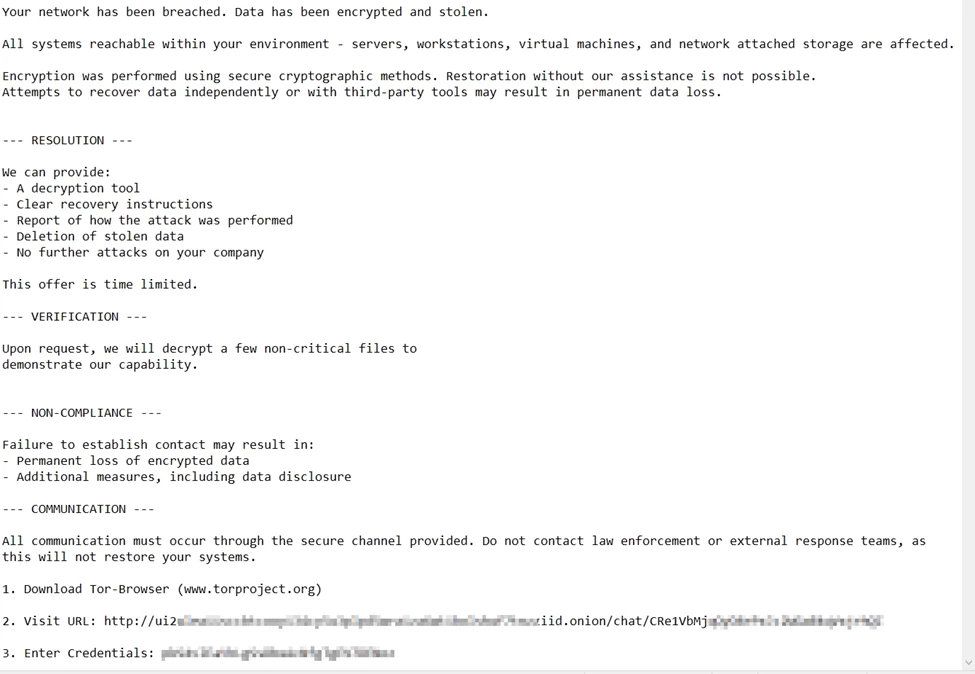
The ransom note placed on the system provides instructions for contacting the attackers through a Tor-based onion site to negotiate payment. Victims are offered free decryption of a small file as proof of capability, a credibility-building tactic commonly associated with LockBit affiliates. Initial ransom demands observed in this campaign begin at approximately $50,000 USD, with amounts increasing based on the size, sector, and perceived operational value of the victim organization.
This campaign underscores the continued effectiveness of low-effort, high-volume malware distribution when paired with fast-acting ransomware payloads. The return of Phorpiex-driven delivery, combined with LockBit-style extortion tactics under the Global Group branding, highlights how established threat actors continue to recycle proven techniques whenever possible. For defenders, the activity reinforces the importance of attachment execution controls, shortcut file detection, and rapid response, as the window between initial execution and full encryption remains measured in minutes rather than hours.






