Malicious email attacks are actively masquerading as the U.S. Internal Revenue Service. One specifically targeted tax-preparation providers such as CPAs and law firms—groups that routinely handle sensitive taxpayer data. The lure warned recipients that potentially fraudulent returns were filed under their EFIN, the unique number assigned to authorized e-file providers and urged them to download a “transcript reviewer” to verify the returns. However, the link redirected to a non-government site registered only days before the campaign launched, a common hallmark of short-lived phishing infrastructure.
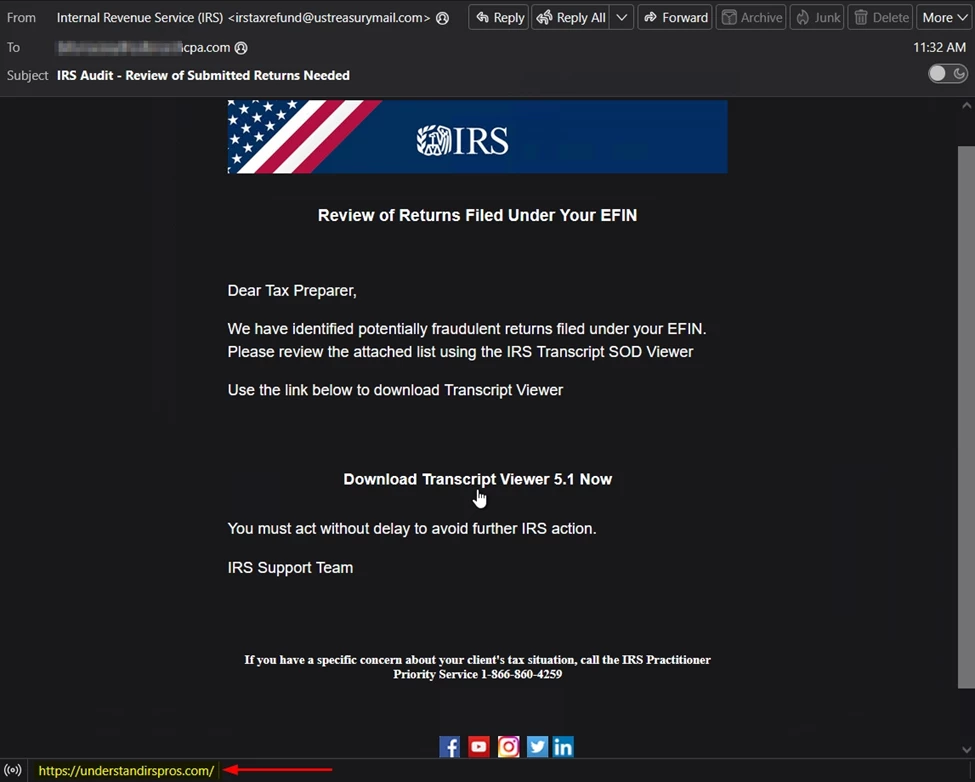
If clicked, the link opened a convincing IRS-themed page that immediately initiated the download of an MSI installer. Once executed, the MSI installed the legitimate PDQ Connect agent, a patch-management and deployment utility used by thousands of organizations worldwide. Hidden inside that package was Rusty Stealer—a Rust-based infostealer known for credential and browser-data theft—which then fetched the ConnectWise Screen Connect remote-access agent. The installation sequence captured in the screenshots also revealed command-line calls to the Windows Volume Shadow Copy Service (VSS) API and vssadmin utilities, behavior commonly linked to ransomware staging. This suggests the attackers were not merely harvesting credentials but potentially preparing the environment for encryption or data-wiping operations.
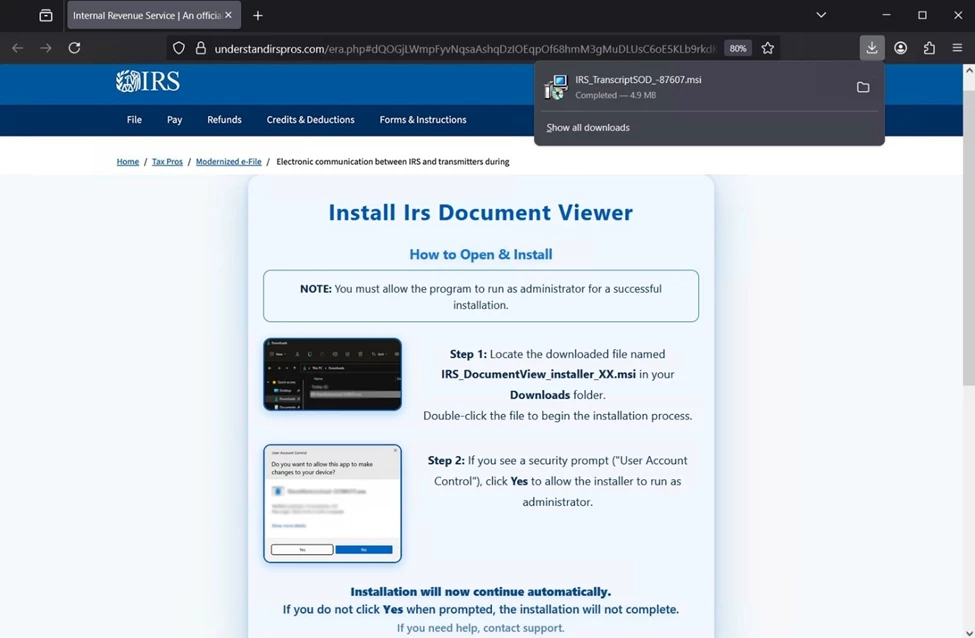
During analysis, we also observed Chinese OLE stream markers embedded within the installer metadata, supporting the theory that this build originated from tooling associated with East-Asian threat clusters. Combined with the VSS activity, these elements indicate a hybrid intrusion chain capable of escalating from infostealer infection to full ransomware deployment.
Another IRS-themed lure used a third quarter tax report theme to garner the recipient’s attention. Attackers constantly exploit the urgency of tax compliance and the authority of government branding to pressure victims into opening attachments or clicking links, but it is important to note that these attackers are strategically targeting CPA’s and law firms.
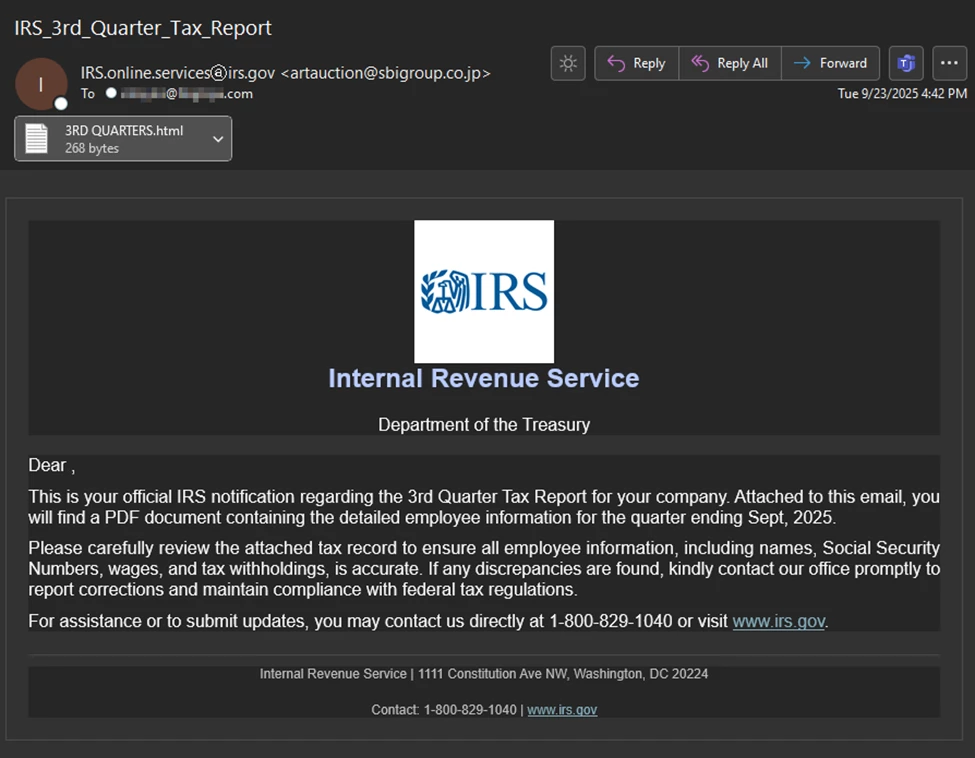
This particular iteration used an attached [.]html file that spoofed irs[.]gov branding, complete with legitimate-looking navigation links pointing back to the real site. Such blending of authentic and malicious assets continues to be a highly effective social-engineering technique.
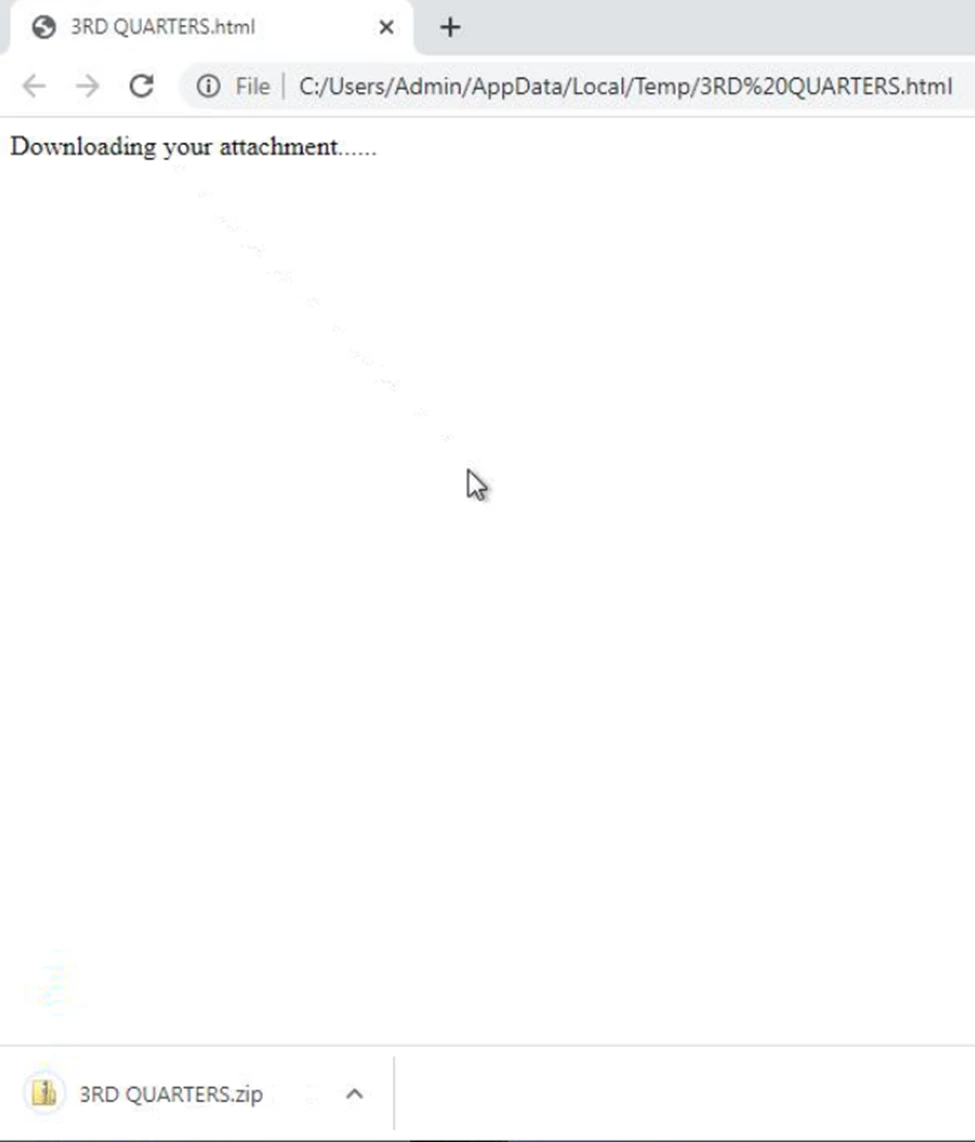
Opening the attached [.]html file automatically triggered a download in the recipient’s default browser, retrieving a [.]zip archive. Extracting the archive revealed an executable payload that installed the Remcos remote access trojan. Once active, Remcos provided attackers with persistent control, keylogging, and data-exfiltration capabilities.
The screenshots show that the ZIP archive’s internal structure and file naming mirrored the campaign theme (for example, “3RD QUARTERS[.]exe”), a subtle touch that likely improved the campaign’s success rate.
Collectively, these IRS-themed attacks demonstrate how threat actors increasingly mix legitimate administrative tools with infostealers and remote-access malware to complicate detection. Yet, each incident helps strengthen industry defenses: security teams can now identify PDQ and Screen Connect misuse patterns faster, update content filters with new IRS phishing templates, and reinforce awareness training for financial and legal professionals ahead of peak tax season




