Threat actors continually search for novel social engineering tactics to avoid arousing suspicion and to disguise their payloads. Sometimes they fail to take the necessary action required to conceal their activity. A recent attack we quarantined was posing as a message regarding joining a YPO Global Leadership Committee. It stated, “a comprehensive Dossier that delves deeper into what being a part of this esteemed committee means,” was attached (via HTML) to the message.
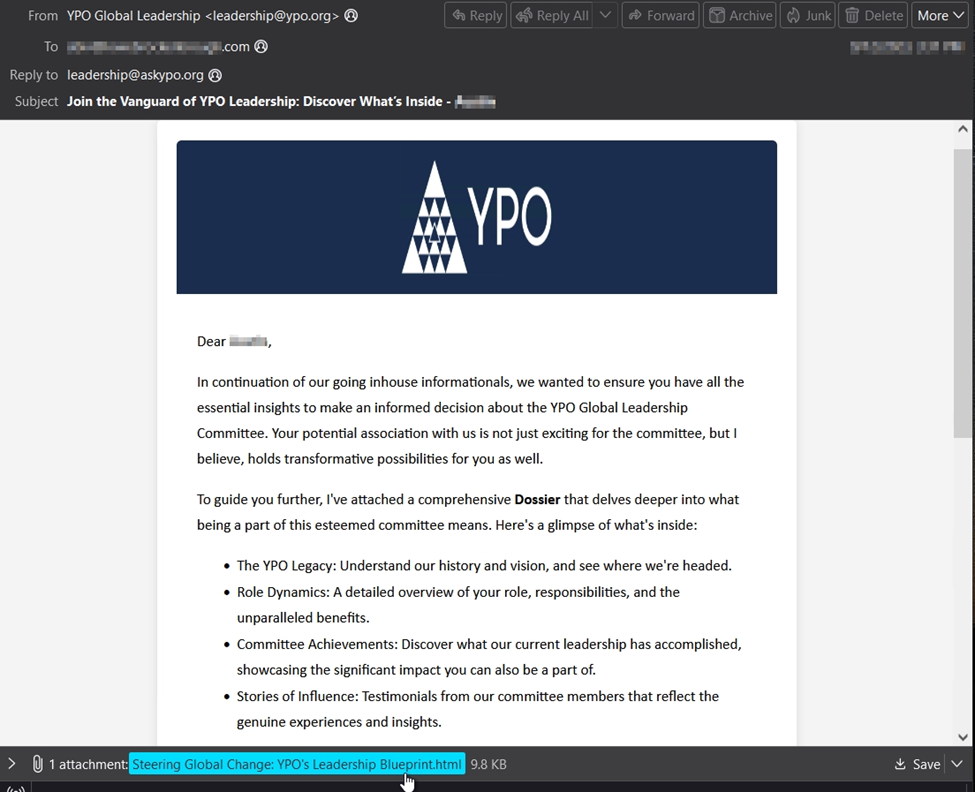
When opening the html attachment, you are presented with a Microsoft OWA themed login portal in your default browser.
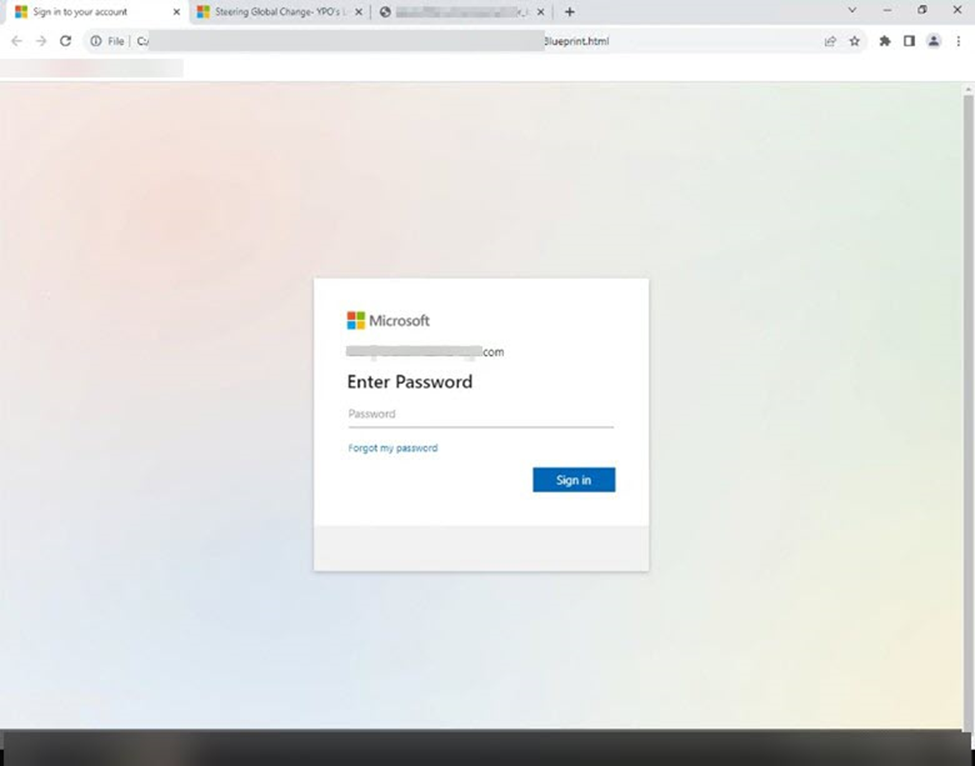
Upon further analysis to determine where the attackers were posting the stolen credentials, we discovered an open directory on the site which showed the compromised data of previous victims who were not using our email threat protection. This open directory, of course, leaves the compromised data open to anyone who goes to look and not just the threat actor. Also contained in the directory was the attackers phish kit. The PHP scripting within revealed they were not only posting credentials to this site for anyone to see. They were also sending the stolen passwords to a discord chat and using API Canary to monitor for their site’s uptime, or any errors generated by it.
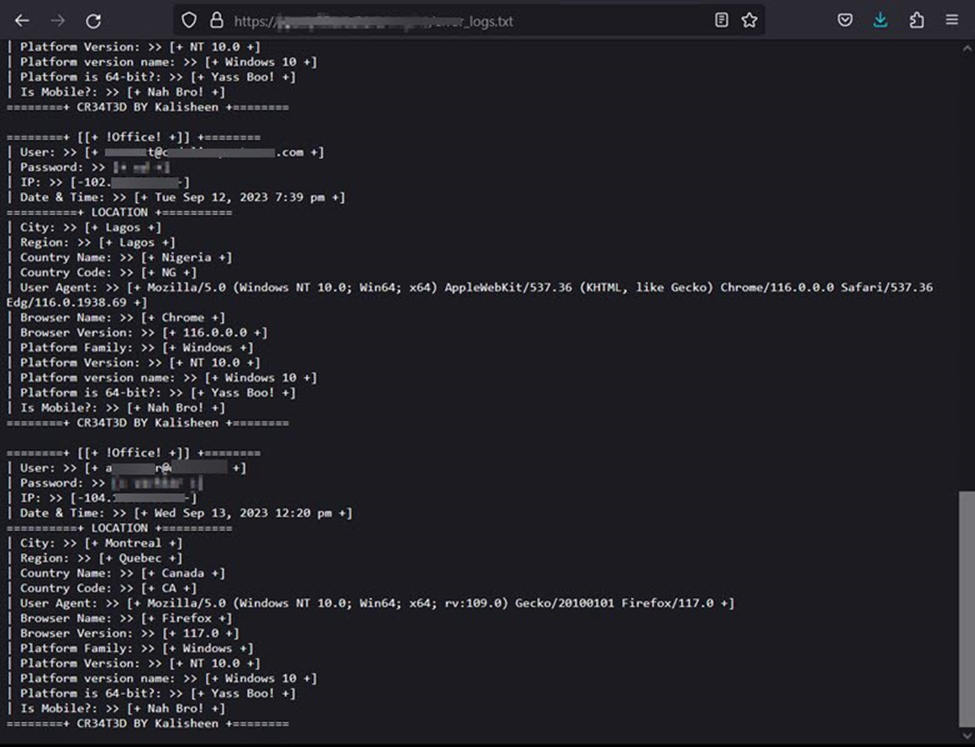
It is not uncommon when we run across this scenario to see victims entering several passwords while attempting to authenticate to the fraudulent site. If you think you have been a victim to this sort of attack it is critical that you, at minimum, immediately change your password to something new/unique and enable MFA. And keep in mind that that your username and password combination will likely be used in other password re-use attacks going forward so it is critical that you take corrective action anywhere else that password is in use.


