LockBit ransomware has resurfaced with a brazen message targeting newly appointed FBI Director Kash Patel. On February 25, 2025, the gang posted a taunting birthday message on their dark web site, offering Patel an encrypted archive supposedly containing classified FBI data. The gang framed the move as a way to "help" Patel expose corruption within the FBI, though cybersecurity analysts already suspect the archive is either publicly available data or a bluff.
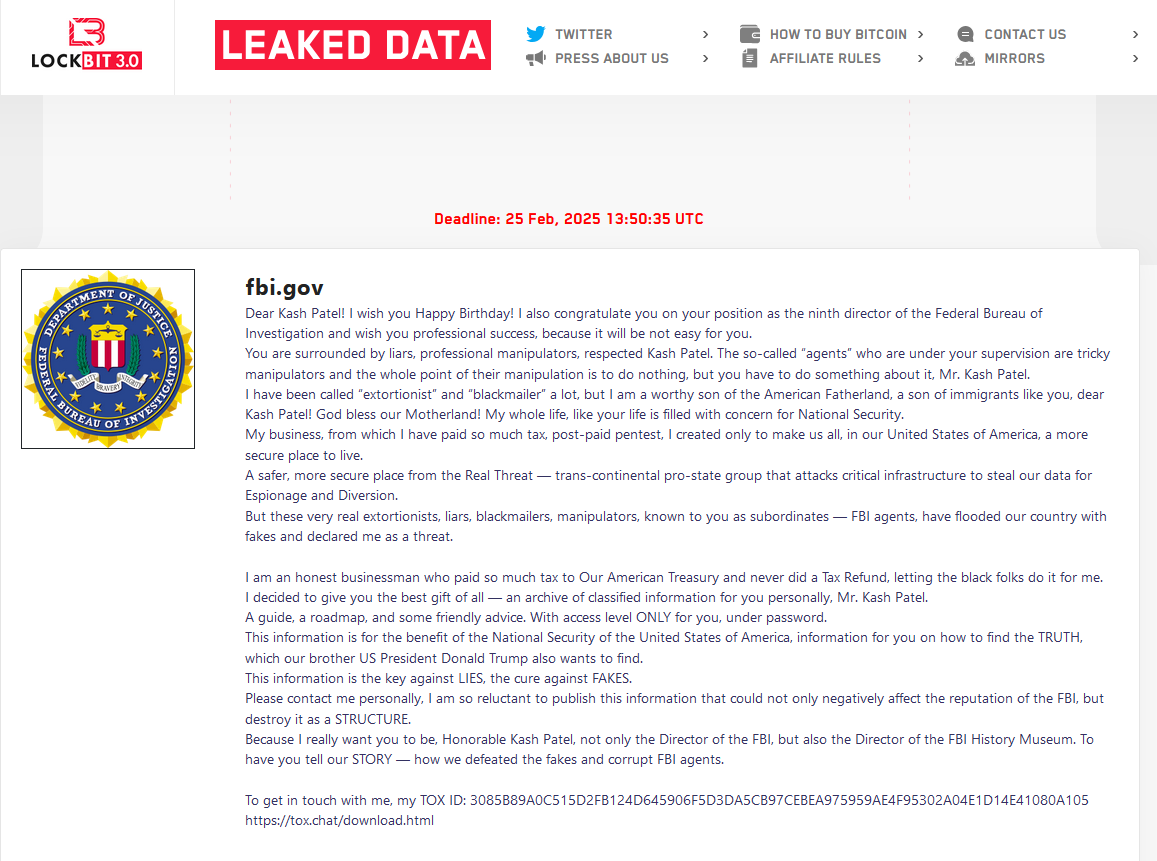
“Dear Kash Patel! I wish you Happy Birthday! I also congratulate you on your position as the ninth director of the Federal Bureau of investigation and wish you professional success, because it will be not easy for you.You are surrounded by liars, professional manipulators, respected Kash Patel. The so-called "agents" who are under your supervision are tricky manipulators and the whole point of their manipulation is to do nothing, but you have to do something about it, Mr. Kash Patel.I have been called "extortionist and "blackmailer" a lot, but I am a worthy son of the American Fatherland, a son of immigrants like you, dear Kash Patel! God bless our Motherland! My whole life, like your life is filled with concern for National Security..." states the message.
This tactic of intertwining cybercrime with politics to generate attention and maintain relevance after suffering setbacks from global law enforcement efforts is not new at all. They have done this before and we anticipate it to continue as long as the leader (Dmitry Khoroshev) remains out of handcuffs.

Here is some previous drama context with LockBit.
Despite major law enforcement operations in 2024 that took down infrastructure, arrested affiliates, and revealed leader identities, LockBit remains operational. This demonstrates the challenge of completely dismantling decentralized ransomware groups. By engaging in public taunts and aligning with political narratives, LockBit shifts ransomware tactics from pure financial extortion to reputation manipulation and disinformation.
Cybersecurity researchers suspect the gang’s primary goal is to reassert dominance in the Ransomware-as-a-Service (RaaS) ecosystem, especially with competition from emerging groups like RansomHub (Previously “BlackCat”). Their upcoming "LockBit 4.0" release suggests an attempt to modernize their ransomware toolkit and attract new affiliates.
Recap of Law Enforcement and Security Response
Operation Cronos, a joint international effort, delivered severe blows to LockBit in 2024:
-
Seized leak sites and took control of infrastructure.
-
Arrested key members, including affiliates in Europe and Canada.
-
Exposed LockBit’s leader, Dmitry Khoroshev, placing a $10 million bounty on his capture.
-
Distributed over 7,000 decryption keys to victims, reducing the gang’s leverage.
-
Sanctioned payments to LockBit, making ransom transactions illegal in several jurisdictions.
Despite these efforts, LockBit’s reemergence confirms that its affiliate model allows operations to continue under different guises. LockBit is proving to be one of the most resilient threat actors seen in our generation and poses difficult challenges for cybersecurity professionals. Their ability to pivot from traditional ransomware attacks to psychological tactics suggests an evolving threat landscape. The group's survival reinforces the need for sustained pressure, including:
-
Continuous threat intelligence monitoring – Tracking new malware variants and tactics.
-
Strengthened law enforcement cooperation – Targeting financial and infrastructure networks supporting ransomware groups.
-
Harsher consequences for cybercriminal safe havens – LockBit affiliates in jurisdictions like Russia remain untouchable.
Recommendations for Defense
Organizations should reinforce cybersecurity postures with:
-
Regular data backups stored offline.
-
Patching vulnerabilities in public-facing systems.
-
Strict access controls & MFA enforcement.
-
Network segmentation to limit ransomware spread.
-
Threat intelligence sharing and collaboration with law enforcement.
-
Incident response planning, including legal and communication strategies.
LockBit’s return and taunt to the FBI serve as a reminder: ransomware groups are adaptable, persistent, and increasingly blending cybercrime with psychological warfare. Organizations and security professionals must stay vigilant, anticipate new tactics, and reinforce defenses against evolving ransomware threats.







