February 5, 2026 By Bill Toulas

Ransomware operators are hosting and delivering malicious payloads at scale by abusing virtual machines (VMs) provisioned by ISPsystem, a legitimate virtual infrastructure management provider.
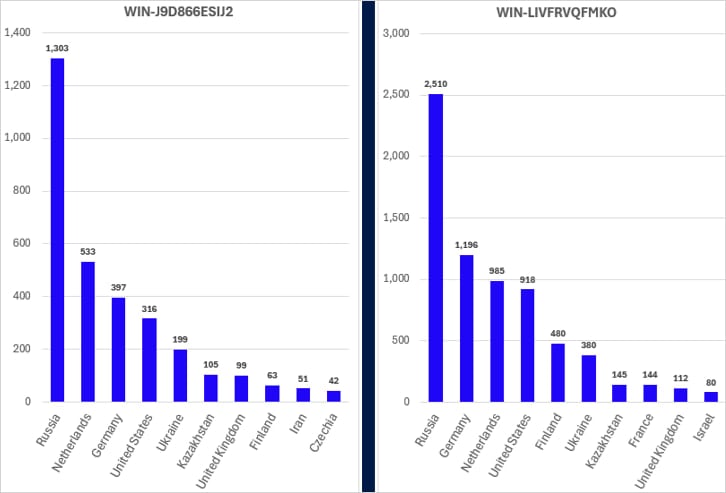
Researchers at cybersecurity company Sophos observed the tactic while investigating recent ‘WantToCry’ ransomware incidents. They found the attackers used Windows VMs with identical hostnames, suggesting default templates generated by ISPsystem’s VMmanager.
Diving deeper, the researchers discovered that the same hostnames were present in the infrastructure of multiple ransomware operators, including LockBit, Qilin, Conti, BlackCat/ALPHV, and Ursnif, as well as various malware campaigns involving RedLine and Lummar info-stealers.
Source: Sophos
ISPsystem is a legitimate software company that develops control panels for hosting providers, used for the management of virtual servers, OS maintenance, etc. VMmanager is the company’s virtualization management platform used to spin up Windows or Linux VMs for customers.


