- Home
- Community overview
- Welcome
- Tech Talk
- How Well is Your System Protected?? --Five Simple Test from AMTSO
How Well is Your System Protected?? --Five Simple Test from AMTSO
- July 6, 2013
- 119 replies
- 456 views
- New Voice
If you want to check whether your Webroot defences are working properly, AMTSO has a series of tests you can perform. These are relatively simple, which will check to see whether your browser, operating system and other software are configured to block malicious and drive-by downloads, and phishing attacks.
I ran the tests on my systems, and Webroot scored 5/5 on every computer.
http://www.amtso.org/feature-settings-check.html
119 replies
- Moderator
- July 6, 2013
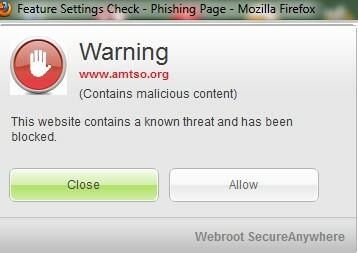
Mine failed on the Phishing page despite the Webshield being on. 😠
- Gold VIP
- July 6, 2013
Also can you Save a Scan log and look near the end and you should see something like this.
Daniel
Sat 06-07-2013 10:59:46.0434 Blocked website: http://www.amtso.org/feature-settings-check-phishing-page.html
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0100007F.17856 - 0100007F.18112]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0100007F.18112 - 0100007F.17856]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.17858 - 9C8E7D4A.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.18882 - 0FE7A7D1.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.19138 - 7C2BC2AD.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.20162 - 7B2BC2AD.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.21442 - 8DE27D4A.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.21954 - 7A2BC2AD.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.22466 - 5DF94740.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.22978 - 63F94740.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.451 - 5671B205.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.963 - 5671B205.20480]
Sat 06-07-2013 14:09:45.0948 Blocked website: http://www.amtso.org/feature-settings-check-drive-by-download.html
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0100007F.11712 - 0100007F.11968]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0100007F.11968 - 0100007F.11712]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35008 - 6DE27D4A.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35264 - 4D2BC2AD.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35520 - 5DF94740.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35776 - 2354B942.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.26561 - 9DC17D4A.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.27073 - 0FE7A7D1.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.27329 - 9CE27D4A.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.28353 - 9BE27D4A.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.15810 - 5671B205.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.16322 - 5671B205.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.18626 - FAEE28BC.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.18882 - FAEE28BC.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.19138 - FAEE28BC.20480]
Sat 06-07-2013 14:10:43.0425 Infection detected: c:usersdanielappdatalocal emp5skg3z6y.exe.part [MD5: 0BB291750D42B911EA63FB71D180927C] [3/00080000] [W32.Trojan.Gen]
Sat 06-07-2013 14:10:43.0425 File blocked in realtime: c:usersdanielappdatalocal emp5skg3z6y.exe.part [MD5: 0BB291750D42B911EA63FB71D180927C, Size: 33280 bytes] [524288/00000003] [W32.Trojan.Gen]
Sat 06-07-2013 14:10:46.0467 Infection detected: c:usersdanieldownloadspotentiallyunwanted.exe [MD5: 0BB291750D42B911EA63FB71D180927C] [3/00080000] [W32.Trojan.Gen]
Sat 06-07-2013 14:10:46.0467 File blocked in realtime: c:usersdanieldownloadspotentiallyunwanted.exe [MD5: 0BB291750D42B911EA63FB71D180927C, Size: 33280 bytes] [524288/00000003] [W32.Trojan.Gen]
Sat 06-07-2013 14:11:57.0526 Infection detected: c:usersdanieldownloadscloudcar.exe [MD5: 3FB121FBBCCB27969668CC36D0A8F15B] [3/00080000] [W32.Malware.Heur.Dkvt]
Sat 06-07-2013 14:11:57.0526 File blocked in realtime: c:usersdanieldownloadscloudcar.exe [MD5: 3FB121FBBCCB27969668CC36D0A8F15B, Size: 7178 bytes] [524288/00000003] [W32.Malware.Heur.Dkvt]
Sat 06-07-2013 14:12:55.0029 Infection detected: c:usersdanielappdatalocal emplrqho0qa.com.part [MD5: 44D88612FEA8A8F36DE82E1278ABB02F] [29/00080200] [(null)
Daniel
Sat 06-07-2013 10:59:46.0434 Blocked website: http://www.amtso.org/feature-settings-check-phishing-page.html
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0100007F.17856 - 0100007F.18112]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0100007F.18112 - 0100007F.17856]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.17858 - 9C8E7D4A.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.18882 - 0FE7A7D1.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.19138 - 7C2BC2AD.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.20162 - 7B2BC2AD.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.21442 - 8DE27D4A.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.21954 - 7A2BC2AD.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.22466 - 5DF94740.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.22978 - 63F94740.47873]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.451 - 5671B205.20480]
Sat 06-07-2013 10:59:46.0450 Closed network connection: [0B00A8C0.963 - 5671B205.20480]
Sat 06-07-2013 14:09:45.0948 Blocked website: http://www.amtso.org/feature-settings-check-drive-by-download.html
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0100007F.11712 - 0100007F.11968]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0100007F.11968 - 0100007F.11712]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35008 - 6DE27D4A.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35264 - 4D2BC2AD.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35520 - 5DF94740.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.35776 - 2354B942.47873]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.26561 - 9DC17D4A.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.27073 - 0FE7A7D1.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.27329 - 9CE27D4A.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.28353 - 9BE27D4A.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.15810 - 5671B205.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.16322 - 5671B205.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.18626 - FAEE28BC.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.18882 - FAEE28BC.20480]
Sat 06-07-2013 14:09:45.0948 Closed network connection: [0B00A8C0.19138 - FAEE28BC.20480]
Sat 06-07-2013 14:10:43.0425 Infection detected: c:usersdanielappdatalocal emp5skg3z6y.exe.part [MD5: 0BB291750D42B911EA63FB71D180927C] [3/00080000] [W32.Trojan.Gen]
Sat 06-07-2013 14:10:43.0425 File blocked in realtime: c:usersdanielappdatalocal emp5skg3z6y.exe.part [MD5: 0BB291750D42B911EA63FB71D180927C, Size: 33280 bytes] [524288/00000003] [W32.Trojan.Gen]
Sat 06-07-2013 14:10:46.0467 Infection detected: c:usersdanieldownloadspotentiallyunwanted.exe [MD5: 0BB291750D42B911EA63FB71D180927C] [3/00080000] [W32.Trojan.Gen]
Sat 06-07-2013 14:10:46.0467 File blocked in realtime: c:usersdanieldownloadspotentiallyunwanted.exe [MD5: 0BB291750D42B911EA63FB71D180927C, Size: 33280 bytes] [524288/00000003] [W32.Trojan.Gen]
Sat 06-07-2013 14:11:57.0526 Infection detected: c:usersdanieldownloadscloudcar.exe [MD5: 3FB121FBBCCB27969668CC36D0A8F15B] [3/00080000] [W32.Malware.Heur.Dkvt]
Sat 06-07-2013 14:11:57.0526 File blocked in realtime: c:usersdanieldownloadscloudcar.exe [MD5: 3FB121FBBCCB27969668CC36D0A8F15B, Size: 7178 bytes] [524288/00000003] [W32.Malware.Heur.Dkvt]
Sat 06-07-2013 14:12:55.0029 Infection detected: c:usersdanielappdatalocal emplrqho0qa.com.part [MD5: 44D88612FEA8A8F36DE82E1278ABB02F] [29/00080200] [(null)
- Moderator
- July 6, 2013
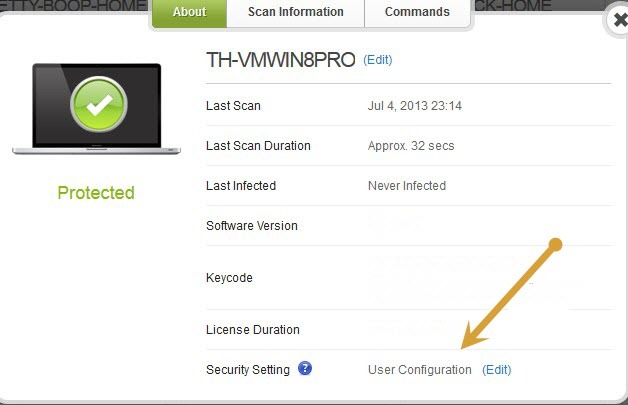
It is working now. I am using Firefox as always for me. I did change my security settings to max on my on-line console and that has sorted it but it did take quite a while for the changes to work down to the computer. It was set at the user config setting and it must have been that which was stopping it working.
This leads me to another question now though.
Is it possible using the on-line console to change the time of the scheduled scan, I have looked and cannot find it.
This leads me to another question now though.
Is it possible using the on-line console to change the time of the scheduled scan, I have looked and cannot find it.
- Gold VIP
- July 6, 2013
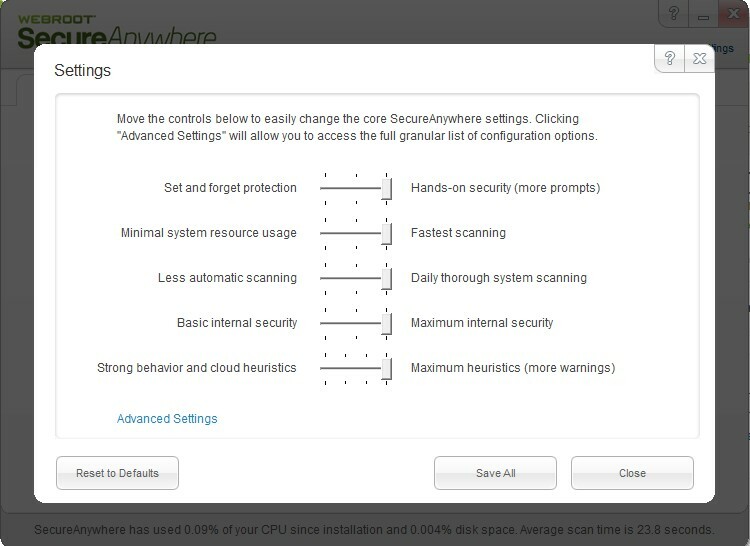
Yes it does when it communicates with the Cloud but I leave it at User Configuration and go through the settings and move the sliders all to right side.@ wrote:
It is working now. I am using Firefox as always for me. I did change my security settings to max on my on-line console and that has sorted it but it did take quite a while for the changes to work down to the computer. It was set at the user config setting and it must have been that which was stopping it working.
This leads me to another question now though.
Is it possible using the on-line console to change the time of the scheduled scan, I have looked and cannot find it.
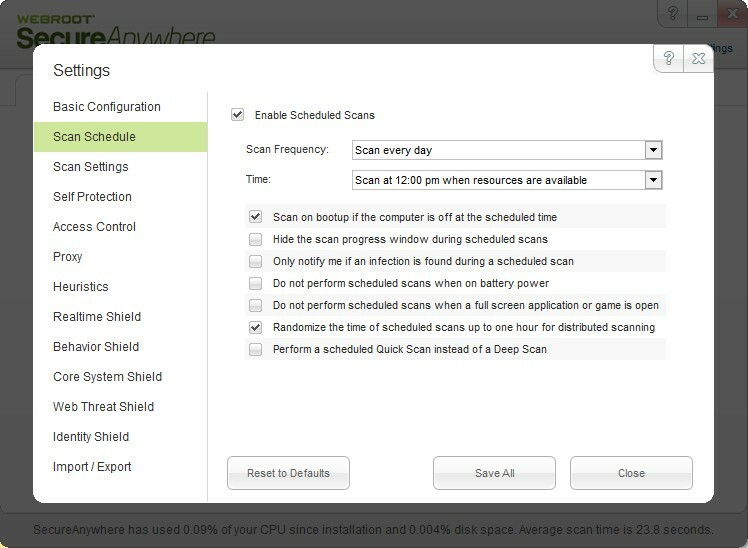
And no you can't you have to go into Advance settings and set the scan schedule second picture.
- Moderator
- July 6, 2013
I have been changing it via the scan schedule inside the scan window but I have just tried it via the advanced settings section. I think I tried that way and it has always reset itself to 8am when I would prefer it at about 7pm when I know it switched on.
This is what I get when I try to change it via the scan schedule page:
This is what I get when I try to change it via the scan schedule page:
- Moderator
- July 6, 2013
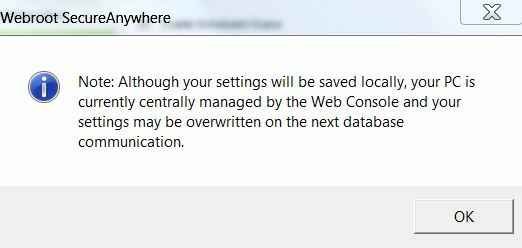
Yes I have just tried it that way and it resets back to 8am. In fact I cannot see a way of selecting a time if it is managed by the Web Console.
- Gold VIP
- July 6, 2013
Because you have it set in the online console go put it back to User Configuration and do a few scans and then change it and it should stick it usually takes 20 to 30 minutes so you might have to try a few times.@ wrote:
Yes I have just tried it that way and it resets back to 8am. In fact I cannot see a way of selecting a time if it is managed by the Web Console.
Daniel
- Gold VIP
- July 6, 2013
Let us know when it sticks! ;)@ wrote:
OK I will try that Daniel.
Daniel
- Community Leader
- July 7, 2013
I would have loved to participate in this one, but I still can't use WSA on my Laptop! Hopefully I will be able to relocate soon so I can get my 8 desktops out of storage! It's interesting to see the results of others though. 🙂
- Community Leader
- July 12, 2013
If you can read this page, it indicates either:
Webroot is not listed on the AMTSO page as software that supports this feature.
In WSA "Block phishing" is enabled. Perhaps this feature only works with Secure (HTTPS) websites as "Block phishing" is listed on the "Protected Websites" page.
- Your Anti-Malware solution is not (yet) supporting this Feature Settings Check
- Your Anti-Malware solution's Anti-Phishing feature is not enabled or misconfigured.
Webroot is not listed on the AMTSO page as software that supports this feature.
In WSA "Block phishing" is enabled. Perhaps this feature only works with Secure (HTTPS) websites as "Block phishing" is listed on the "Protected Websites" page.
- Bronze VIP
- July 21, 2013
An answer fothcoming to above post?
..........and make yourself a Great Day! Cheers, Lyle
- Popular Voice
- July 21, 2013
Thanks for the tests...always appreciate that kind of info!!!
Rompin Raider WSA Complete Windows10 MacOS Sierra
- Bronze VIP
- July 23, 2013
Feature Settings Check - Phishing Page
If you can read this page, it indicates either:
Your Anti-Malware solution is not (yet) supporting this Feature Settings Check
or
Your Anti-Malware solution's Anti-Phishing feature is not enabled or misconfigured.
If your vendor's name appears below, your Anti-Malware product is supports this Feature Settings Check page. If your system failed the test, click on the name of the vendor for instructions explaining how to enable the feature in your product. If your vendor does not have a dedicated page and no hyperlink is present, please contact the support department of your vendor.
Same here opera 12.15 Browser??
If you can read this page, it indicates either:
Your Anti-Malware solution is not (yet) supporting this Feature Settings Check
or
Your Anti-Malware solution's Anti-Phishing feature is not enabled or misconfigured.
If your vendor's name appears below, your Anti-Malware product is supports this Feature Settings Check page. If your system failed the test, click on the name of the vendor for instructions explaining how to enable the feature in your product. If your vendor does not have a dedicated page and no hyperlink is present, please contact the support department of your vendor.
Same here opera 12.15 Browser??
..........and make yourself a Great Day! Cheers, Lyle
- Retired Webrooter
- July 23, 2013
/// JimM /// /// Former Community Manager - Now Humble Internet Citizen/// /// Also Formerly a Technical Support Escalations Engineer ///
- Community Leader
- October 25, 2013
My score is 5/5, SecureAnywhere blocks every possible danger immediately:D
WEBROOT® SecureAnywhere™ Internet Security Complete Beta macOS Sierra & Windows 10 Pro 64
- Popular Voice
- January 22, 2014
Know that this is a slightly older thread but I just tested this with the new Web Filter (on v8.0.4.46 / WFE 1.0.0.23 / WPM 2.5.0) on FF v26.0 and the Phishing Page test is first allowed and then blocked (actually, the whole site got blocked until I reloaded the tab) AND then the test page / whole site is allowed again. Is this just not working with the BrightCloud engines or ?????
Thanks for the help.
(Page is here: hxxp://www.amtso.org/feature-settings-check-phishing-page.html)
Thanks for the help.
(Page is here: hxxp://www.amtso.org/feature-settings-check-phishing-page.html)
Win7 x86 WSA , Win10 x64 WSA BETA? , Brain 2.3, MCShield Proud Graduate of Geeks To Go
- Community Leader
- January 22, 2014
Hi dbrisendine,
Can you post a screenshot of the block message or upload it to TinyPic if you can't post images here? This sounds like it may be the old web filer as I never get the blocks at all with the new filter.
Thanks,
Shran 😉
Can you post a screenshot of the block message or upload it to TinyPic if you can't post images here? This sounds like it may be the old web filer as I never get the blocks at all with the new filter.
Thanks,
Shran 😉
- Popular Voice
- January 23, 2014
Sorry, I don't have a screen shot of the Blocking Web page but I can tell you it is the new Web Filtering doing the blocking (Orange and Black message box on the page) as I've never had the old web filter running on this system or my version of WSAC. It was weird; blocked the entire site not just the Phishing Test page, but now I can not get the Web Filter to block it again. That's why I was asking here; inconsistent results.
Win7 x86 WSA , Win10 x64 WSA BETA? , Brain 2.3, MCShield Proud Graduate of Geeks To Go
- New Voice
- March 5, 2014
I know this is a bit old, but as a new Webroot user, can anyone explain why some users are passing the Phishing Site test and others, such as myself, are failing it? I've looked at my settings and can't see anything unusual, but I end up with the same screen as provided previously; basically suggesting either my protection isn't working or isn't set up right.
Thanks!
UPDATE: No threat is detected with Metro IE, but when I go to the link using desktop IE, I do get the warning from Webroot. However, from the desktop and Chrome, I get no such warning. Is there some setting that I'm missing?
Thanks!
UPDATE: No threat is detected with Metro IE, but when I go to the link using desktop IE, I do get the warning from Webroot. However, from the desktop and Chrome, I get no such warning. Is there some setting that I'm missing?
WSA Windows 8.1 64b/Mac OSX Mavericks/Some GNU/Linux stuff
- Gold VIP
- March 5, 2014
Hello liontamer and Welcome to the Webroot Community Forums!
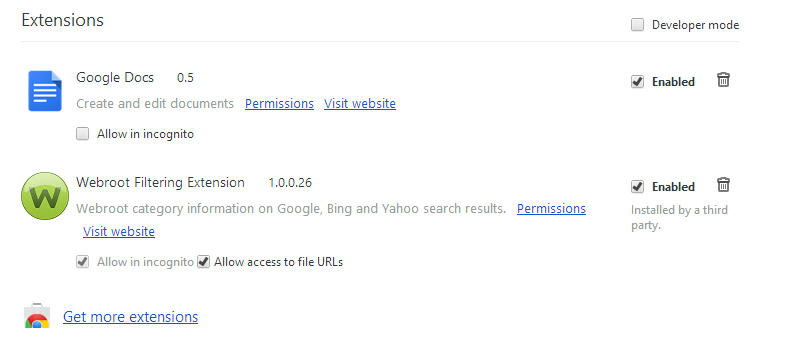
Can you check your Browsers Extensions and look for the Webroot Filtering Extension and the version like I have 1.0.0.26 it should show in IE, Chrome, Firefox & Safari are only supported and please let us know. And I will check and test Metro IE.
Metro IE11
"With very few exceptions, it doesn’t allow plug-ins or add-in programs, extensions, toolbars, or anything that may gum up the works. Yes, that means you can’t use Microsoft Silverlight, Microsoft ActiveX controls, the Java Runtime Environment (which Microsoft used to distribute as part of Windows), the Internet Explorer Developer Toolbar or the Bing Toolbar, (er, Bing Bar), or the MSN Toolbar.In fact, you can’t even use Microsoft add-ins, plugins, or toolbars, much less those from other companies like Ask or Yahoo!.By getting rid of all the junk (including many pieces of flotsam created, distributed, and promoted by Microsoft), Metro IE is considerably faster, more uniform, easier on the battery, and much more secure than any other version of IE, ever."
http://www.dummies.com/how-to/content/the-two-faces-of-internet-explorer-in-windows-81.html
And I have the Extensions in IE11 & Chrome Win 8.1 Pro x64!
Thanks,
TH
Can you check your Browsers Extensions and look for the Webroot Filtering Extension and the version like I have 1.0.0.26 it should show in IE, Chrome, Firefox & Safari are only supported and please let us know. And I will check and test Metro IE.
Metro IE11
"With very few exceptions, it doesn’t allow plug-ins or add-in programs, extensions, toolbars, or anything that may gum up the works. Yes, that means you can’t use Microsoft Silverlight, Microsoft ActiveX controls, the Java Runtime Environment (which Microsoft used to distribute as part of Windows), the Internet Explorer Developer Toolbar or the Bing Toolbar, (er, Bing Bar), or the MSN Toolbar.In fact, you can’t even use Microsoft add-ins, plugins, or toolbars, much less those from other companies like Ask or Yahoo!.By getting rid of all the junk (including many pieces of flotsam created, distributed, and promoted by Microsoft), Metro IE is considerably faster, more uniform, easier on the battery, and much more secure than any other version of IE, ever."
http://www.dummies.com/how-to/content/the-two-faces-of-internet-explorer-in-windows-81.html
And I have the Extensions in IE11 & Chrome Win 8.1 Pro x64!
Thanks,
TH
- New Voice
- March 5, 2014
Thanks for your response. I've found:
IE Desktop does have the Webroot filtering extension enabled.
Google Chrome does not have the extension even noted. There is an option for Webroot Password extension however, which is not enabled.
Bob
IE Desktop does have the Webroot filtering extension enabled.
Google Chrome does not have the extension even noted. There is an option for Webroot Password extension however, which is not enabled.
Bob
WSA Windows 8.1 64b/Mac OSX Mavericks/Some GNU/Linux stuff
- Gold VIP
- March 5, 2014
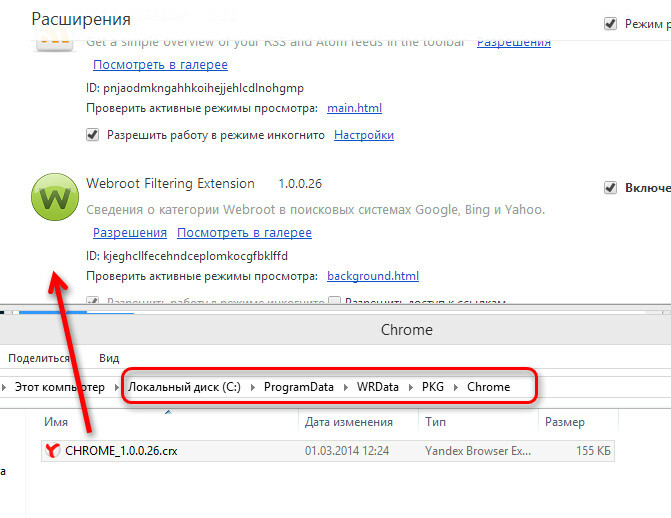
Hello liontamer and Welcome to the Webroot Community Forums!@ wrote:
Google Chrome does not have the extension even noted.
Extension is disabled or not installed?
If the extension is not installed(problems)
Try to install the extension "dragging"
First turn on the display of hidden folders
Control Panel-> Folder Options-> View-> Set - Show hidden files, folders.
Thank you
Best regard, Petr.
Helpful Webroot Links: Download (PC) | Download (Best Buy Subscription) | Submit Support Ticket | Account Console | User_Guides | BrightCloud URL lookup
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
Scanning file for viruses.
Sorry, we're still checking this file's contents to make sure it's safe to download. Please try again in a few minutes.
OKThis file cannot be downloaded
Sorry, our virus scanner detected that this file isn't safe to download.
OK