Most of this information can also be found in the user guide.
Features, Features, and More Features:
The Identity Shield is a feature-rich identity protection system that protects users in a multitude of ways. Most of these settings are accessed via “View/Edit Protected Websites,” so that’s where we’ll start. These settings are all uniquely configurable for HTTPS, HTTP, Facebook, Twitter, and custom sites.
Here are some detailed explanations of what all of these features do for you:
Website protection optionsDescription
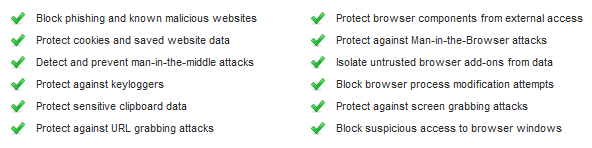
Block phishing and known malicious websitesAlerts you to phishing sites and other malicious sites listed in our Webroot database. Phishing is a fraudulent method used by criminals to steal personal information. Typical scams might include websites designed to resemble legitimate sites, such as PayPal or a banking organization, which trick you into entering your credit card number.
Protect cookies and saved website dataAlerts you if a malicious program attempts to gather personal data from cookies installed on your computer. Cookies are small bits of text generated by a web server and then stored on your computer for future use. Cookies can contain everything from tracking information to your personal preferences.
Detect and prevent man-in-the middle attacksAlerts you if a server is redirecting you to a malicious website (man-in-the-middle attack). This is a method of intercepting communications between two systems and stealing data.
Protect against keyloggersStops keyloggers from recording keystrokes on your computer. Keyloggers may monitor emails, chat room dialogue, instant message dialogue, websites visited, usernames, passwords, programs run, and any other typed entries. They have the ability to run in the background, hiding their presence.
Protect sensitive clipboard dataStops malware programs from capturing clipboard data. The clipboard is a utility that allows you to cut and paste stored data between documents or applications.
Protect against URL grabbing attacksHides your web browsing activity from malware that attempts to log the websites you visit.
Protect browser components from external accessHides your web browsing activity from malware that attempts to modify your browser with memory injection and other behind-the-scenes attacks.
Protect against Man-in-the-Browser attacksBlocks a malicious toolbar from stealing data. A man-in-the-browser attack is a Trojan that infects a web browser. It can modify pages and the content of your transactions without being detected.
Isolate untrusted browser add-ons from dataBlocks a browser add-on (browser helper object) from stealing data. While most browser add-ons are legitimate, some can display ads, track your Internet activity, or hijack your home page.
Block browser process modification attemptsAnalyzes browser memory to see if code injection is taking place.
Protect against screen grabbing attacksBlocks a malicious program from viewing and capturing your screen content.
Block suspicious access to browser windowsBlocks a malicious program from viewing and capturing data in Windows components.
When the Identity Shield is actively protecting you, you'll see this little padlock icon in your system tray:
Low-Level Operation
The Identity Shield operates at a very low level in Windows. To take an example, the way this works for protecting your clipboard data is that WSA steps inbetween a program that is asking for that clipboard data and the clipboard itself. When the program requests that data, WSA checks against its database of all known programs to see if the program is legitimate or not. If the program is not a confirmed, good program, that action is blocked. In the same way, WSA protects against screengrabbers, keyloggers, and URL stealing attacks. Similar protection is utilized in protecting against cookie tampering and code injection threats.
Man-In-The-Browser
A man-in-the-browser attack is another type of attack that tries to pilfer your information. The way these sort of attacks work is that a web browser itself becomes infected by a trojan. The browser will then modify the page contents, sometimes to include fields that wouldn't otherwise exist or repurpose existing fields to do something other than what they were intended for. This is a common attack vector for banking websites for instance. In a recent demonstration, our Director of Security Intelligence, Grayson Milbourne, showed off a threat that modified a standard bank login page to include a password field that didn't otherwise exist. The purpose of this threat was to get these banking customers to enter their username and password in some boxes that looked very legitimate but really weren't. That data would then be sent off to the malware authors, who would use it to access bank accounts. The Identity Shield provides a secondary layer of protection against this sort of threat. The primary protection is provided by the Realtime Shield, but in the rare event that a new threat gets through that shield as an Unknown file (rather than being flagged as a Bad file), the Identity Shield still provides a secondary layer of protection against this kind of threat.
URL Reputation
URL reputation is also a factor taken into account when protecting against phishing and man-in-the-middle-style attacks. This works in conjunction with the Web Threat Shield.
Not Just Browsers
The Identity Shield protects only web browsers by default, but it can also be configured to protect other applications in the same fashion. Financial management software is one other common usage, but you are limited only by your imagination in terms of which programs you add. The kinds of programs you may wish to add should be ones in which there is some kind of sensitive information in use.
And which browsers are supported you may ask?
The Identity shield supports all of the following browsers:
- Internet Explorer 7.0 and higher (32-bit only)
- Mozilla Firefox 3.6 and higher (32-bit only)
- Google Chrome 10 and higher
- Opera 9 and higher (32-bit only)
- Safari 5.0.1 or higher
Other Settings
If you dig deeper into the settings, you'll also find all of these:
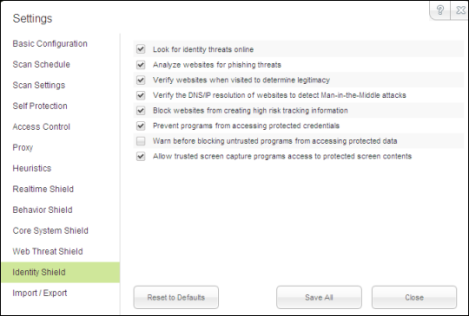
These are the default settings^
The user guide is helpful in explaining what these settings do:
Identity shield settingsDescription
Look for identity threats onlineAnalyzes websites as you browse the Internet or open links. If the shield detects any malicious content, it blocks the site and opens an alert.
Analyze websites for phishing threatsAnalyzes websites for phishing threats as you browse the Internet or open links. If the shield detects a phishing threat, it blocks the site and opens an alert. Phishing is a fraudulent method used by criminals to steal personal information. Typical scams might include websites designed to resemble legitimate sites, such as PayPal or a banking organization, which trick you into entering your credit card number.
Verify websites when visited to determine legitimacyAnalyzes the IP address of each website to determine if it has been redirected or is on our blacklist. If the shield detects an illegitimate website, it blocks the site and opens an alert.
Verify the DNS/IP resolution of websites to detect Man-in-the-Middle attacksLooks for servers that could be redirecting you to a malicious website (man-in-the-middle attack). If the shield detects a man-in-the-middle attack, it blocks the threat and opens an alert.
Block websites from creating high risk tracking informationBlocks third-party cookies from installing on your computer if the cookies originate from malicious tracking websites. Cookies are small bits of text generated by a web server and then stored on your computer for future use. Cookies can contain everything from tracking information to your personal preferences.
Prevent programs from accessing protected credentialsBlocks programs from accessing your login credentials (for example, when you type your name and password or when you request a website to remember them).
Warn before blocking untrusted programs from accessing protected dataOpens an alert any time malware attempts to access data, instead of blocking known malware automatically. (This option is for technical users only; we recommend that you keep this option disabled so the program does not open numerous alerts.)
Allow trusted screen capture programs access to protected screen contentsAllows you to use legitimate screen capture programs, no matter what content is displayed on your screen.
One common question we've received is "What constitutes 'protected credentials?" The answer is that it's a lot of things. Windows stores sensitive information in a lot of places. Browsers do that as well. As a prime example, take a look at this article on how easy it is to break into a browser's stored passwords. The Identity Shield can protect against that.
A New Setting for Business Customers
As of 6/20/2013, there is now an additional setting for business customers in particular. "Identity Shield Compatibility Mode" can be used in any odd situations you may encounter in which standard function of the Idenitty Shield impairs the operation of any Good programs.
From the user guide: "Allows certain applications to run that the Identity shield might block during normal operations. You can enable this option if you notice problems with an application's functions after SecureAnywhere was installed on the endpoint. With this compatibility mode enabled, the endpoint is still protected by the Identity shield's core functionality."
If there are any follow-up questions to this deep dive, please ask away!
(Special thanks to