This Live Blog will be updated with new info on the Emotet malware as we see it evolve.
Botnets have continued to dominate the infection attack chain the past few years. No other type of malware was responsible for delivering more malicious payloads like ransomware, credential stealing trojans, and cryptomining malware. Emotet, which was the most prevalent malware of 2018, held onto that notorious distinction into 2019. Briefly shut down in June 2019, Emotet returned from the dead in September 2019, and still remains the largest botnet to date.
While Emotet is always evolving and still experimenting with new ways to infect victims and their networks, the below is a short summary of what a user would experience when being the target of this very common attack.
Emotet infects users via a malicious script or macro-enabled document that spreads from spam emails. The “urgent notice” emails attempt to persuade the user to open the attachment by saying “you’re being sued”, or “you missed a package”, or “here is the invoice/payment details of your order”. Sometimes they'll even take advantage of the holidays in the form of e-Christmas cards.
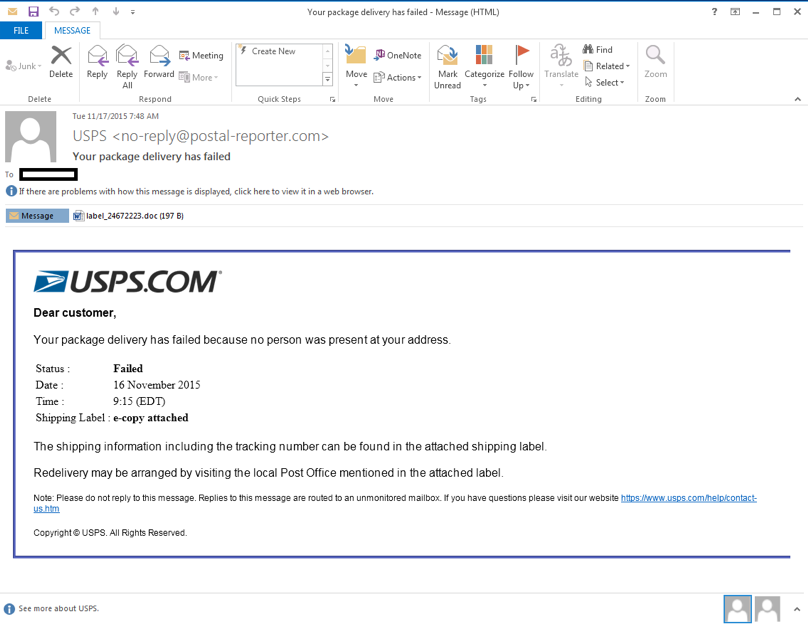
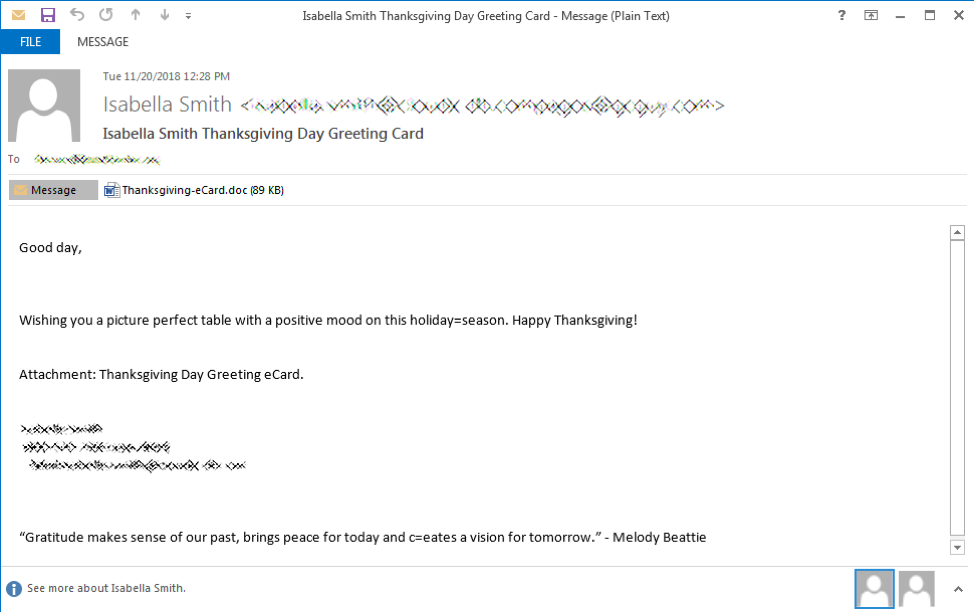
When a user opens the file they'll see a document without the information promised. Instead the script will try to persuade the victim that the document is protected. Next, it'll prompt the victim to click the “enable content” button to view the document.
This is the trick; the 'gotcha'. When the user clicks on the “enable content” button the user has now activated the macro. This will then start the download and execution of the Emotet malware.
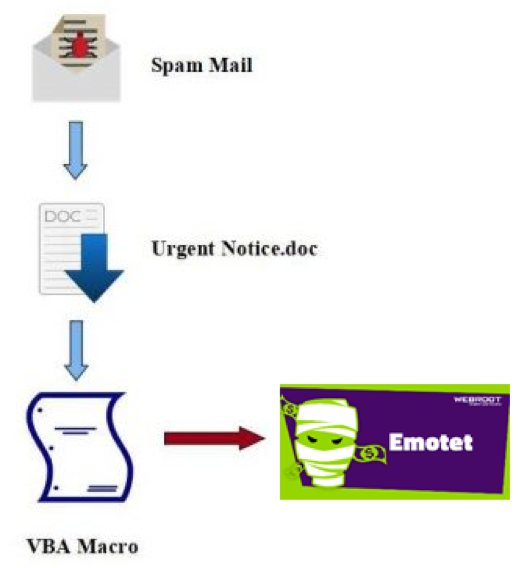
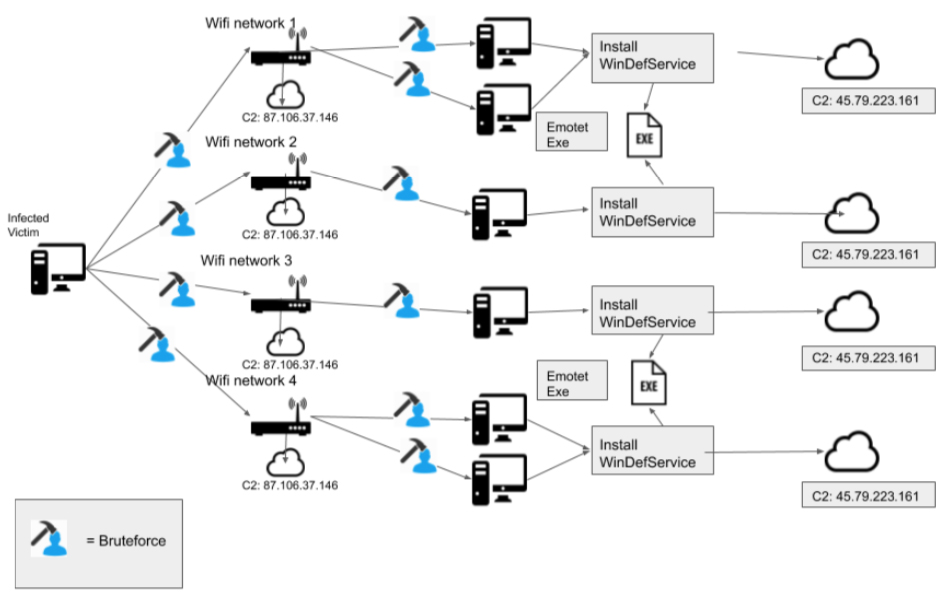
Once infected, Emotet will act as a sensor for the criminal to analyze the environment to “case the joint” if you will. It will run a variety of tasks like:
-
Downloading additional malware
-
Stealing stored passwords
-
Providing remote access to the attackers
-
Deploying a ransomware or cryptomining payload to make money
The in depth analysis of the environments by the hackers using Emotet allow them to know the worth of the data they are stealing/breaching and request much larger ransom payments.
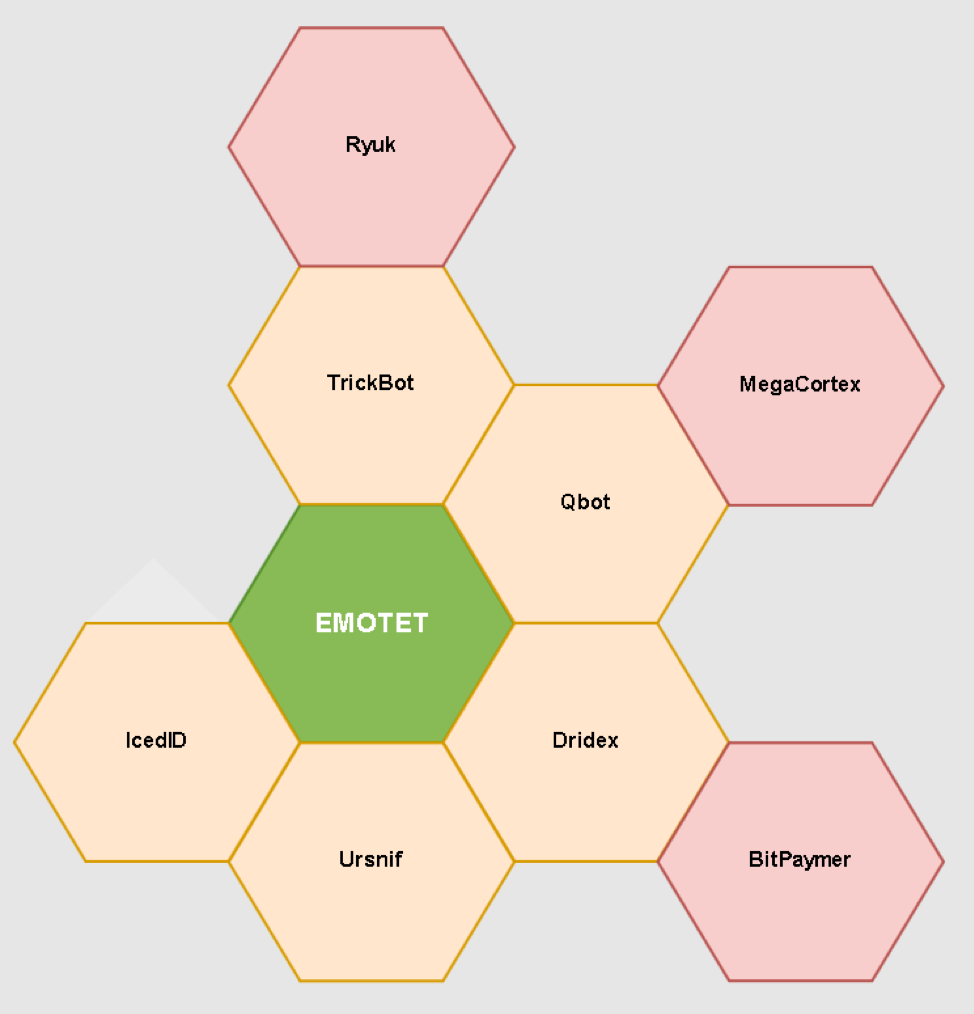
Summary of end result payloads from Emotet
Emotet - Trickbot – Ryuk (“Triple Threat”)
In terms of financial damages this is probably the most successful chain of 2019. It's also worth noting Emotet -> Dridex -> Bitpaymer. Both of these groups (Trickbot / Ryuk and Dridex / Bitpaymer) have shifted to more target/reconnaissance based operations. They assign a value to the targeted network after infection. Then, they'll ransom them for that amount post lateral movement/deployment of their ransomware.
Trickbot/Ryuk
Through the first half of 2019, Trickbot was often delivered as the second stage payload from Emotet. Ryuk infections typically delivered by Trickbot result in mass encryption of entire networks. Trickbot has been partnering with banking Trojan groups like IcedID and Ursif in 2019. Its modular infrastructure makes it a serious threat for any network it infects and, when combined with Ryuk ransomware, it's one of the more devastating targeted attacks of 2019.
Dridex/Bitpaymer
Dridex was once one of the most prominent banking trojans. Now it acts as an implant in the infection chain with the Bitpaymer ransomware and is achieving alarming success. We've observed it also being delivered as a second stage payload off of Emotet.
Cryptomining is an emerging online threat that hides on a computer or mobile device and uses the machine’s resources to “mine” forms of online money known as cryptocurrencies. It uses unused CPU on the machine as discretely as possible without the victims knowledge or consent. And according to Webroot’s research, these attacks rise and fall with the relative market cap of cryptocurrency price.