If 2024 was the year ransomware came roaring back, 2025 was the year it learned your name. Attackers did not just hack networks this year. They hacked people. With artificial intelligence now shaping phishing, voice cloning, and fake job interviews, cybercrime has entered the age of identity warfare.
Stream the Webinar on demand HERE
The New Battlefield
Traditional defenses are losing ground because the battlefield has moved inside the perimeter. Instead of breaking software, threat actors manipulate users and abuse credentials that look legitimate. Breakout times are now measured in seconds, and every stolen password or phone call can open the door to a full-scale breach.
Social engineering, deepfakes, and AI chat tools have turned ordinary interactions into attack vectors. We’re seeing a major spike in credential theft through early 2025, as stolen identities become the preferred gateway for ransomware and data extortion. Once those credentials are compromised, they’re weaponized through targeted attacks and underground markets that trade access like currency.
Follow the Money
Despite stronger defenses and more victims refusing to pay, the ransomware economy remains highly profitable. After spiking earlier in the year, ransom demands and payments have begun to level out, but the overall financial impact continues to climb. Even as some attackers struggle to collect, the most organized operations still negotiate multi-million-dollar settlements with alarming precision.
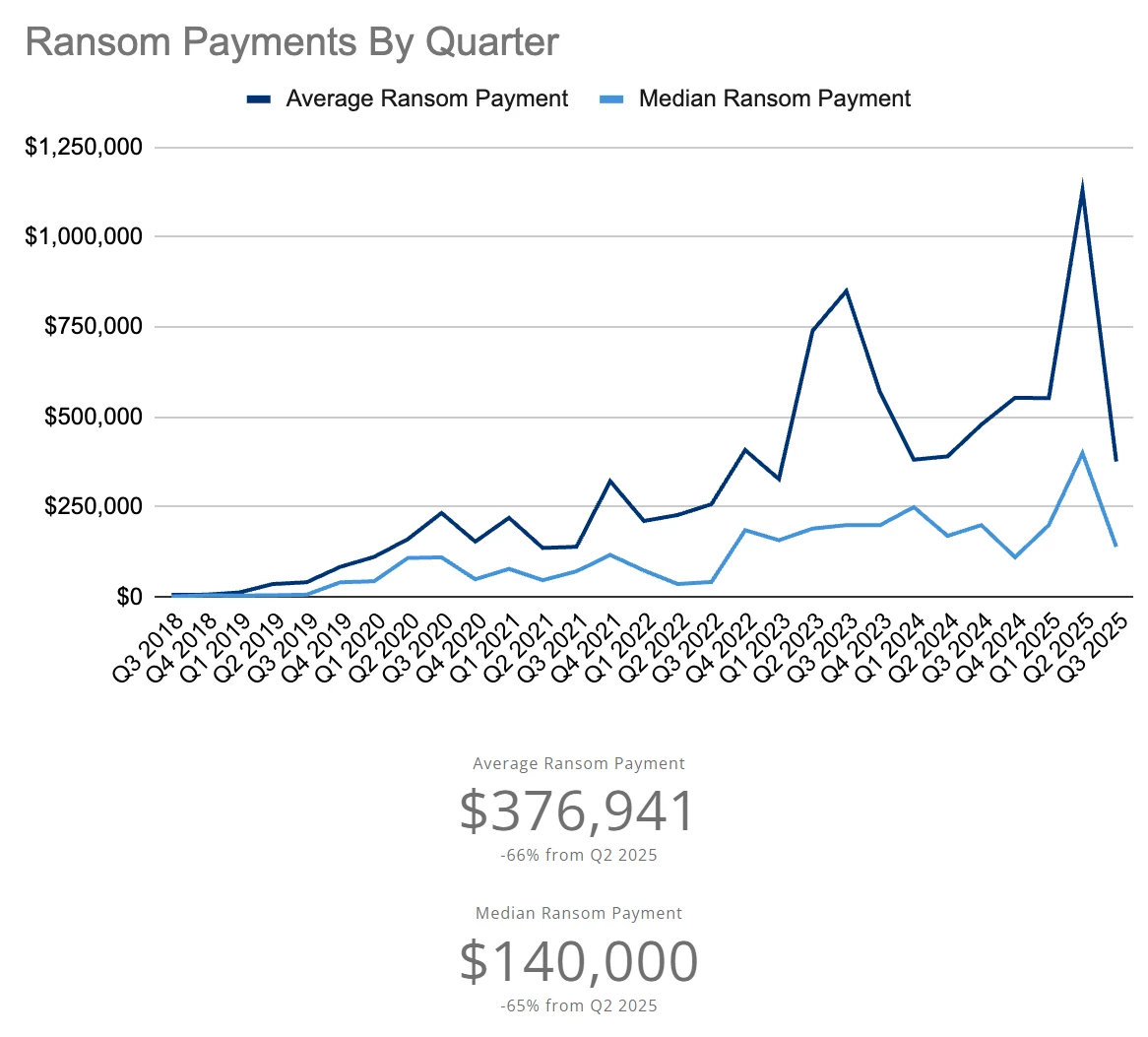
This shift reflects how deeply professionalized ransomware has become. Groups such as Akira and Qilin treat extortion like enterprise sales, targeting organizations that can afford larger payouts and handling negotiations through dedicated affiliates and custom-built negotiation portals.
Ransomware may no longer be breaking new financial records each quarter, but the market has stabilized at historically high levels. The result is a mature extortion economy that continues to thrive on stolen credentials, data theft, and calculated pressure rather than brute-force encryption alone.
The Psychology of Compromise
Even as ransom demands fluctuate, fewer victims are choosing to pay. Over the past several years, the rate of payment has steadily declined as more organizations invest in recovery and refuse to reward extortion.
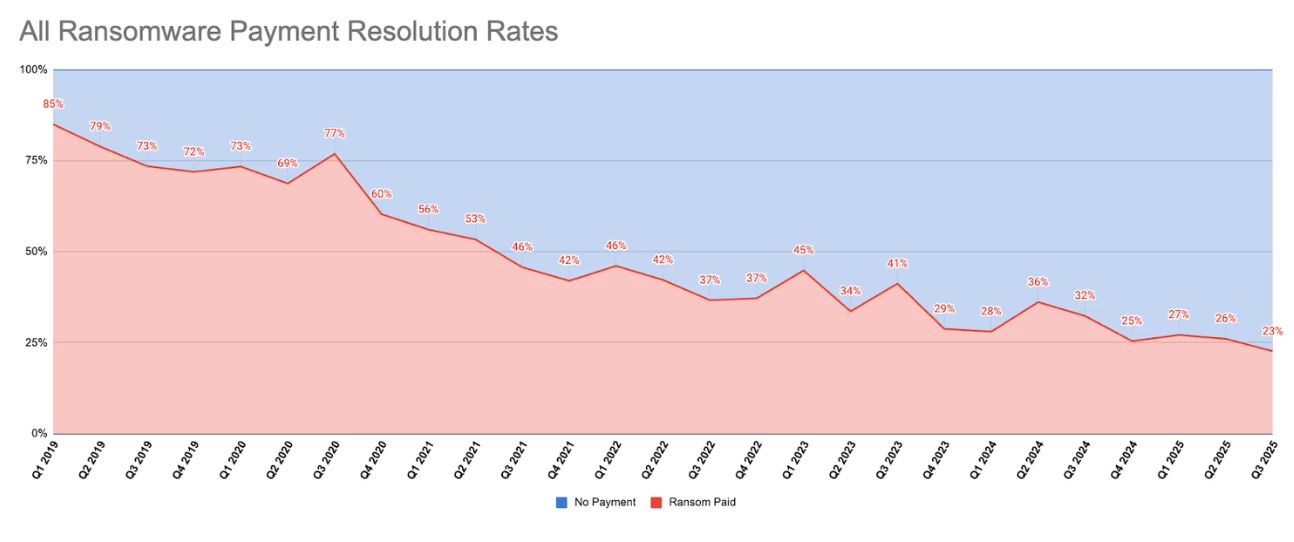
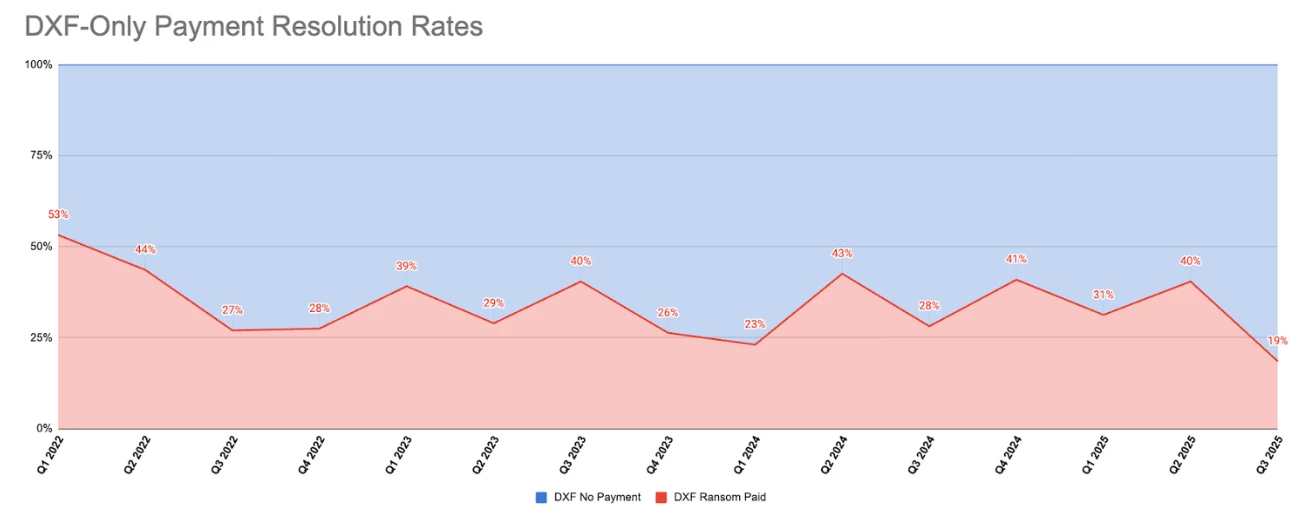
Attackers have adapted by moving from encryption to data theft, stealing and threatening to leak sensitive information instead of locking systems. These data exfiltration only attacks rely on psychological pressure rather than disruption, using the threat of regulatory fines, reputational damage, and customer backlash to force payment.
Recent data shows that even these tactics are starting to lose effectiveness. As more organizations coordinate with law enforcement, strengthen backups, and adopt identity-first security, extortion-based attacks are delivering smaller returns. Each refusal to pay chips away at the ransomware economy and reinforces a broader shift toward collective resilience.
Here are the six groups that defined 2025, innovators of chaos who treated cybercrime like a startup and scaled it globally.
The Nastiest Malware of 2025
Qilin (Agenda) – The Volume Leader

Qilin takes the top spot for 2025 after a relentless year of attacks that pushed hospitals, laboratories, and local governments to the brink. The group executed more than 200 confirmed incidents, averaging one new healthcare breach every week. Their methods are ruthless and efficient, showing no hesitation to disrupt life-critical systems if it increases leverage.
The June 2025 attack on UK pathology provider Synnovis marked a grim milestone. The ransomware crippled diagnostic services for hundreds of thousands of patients, forcing surgery cancellations and delaying cancer treatments. Investigators later confirmed at least one patient death linked to the outage. When the ransom went unpaid, the attackers leaked sensitive medical data, underscoring how human life has become collateral in their business model.
Among their most disturbing innovations was the first “Call Lawyer” feature built directly into a ransomware control panel. The option allowed affiliates to click a button that opened an encrypted chat with a Qilin-provided “negotiation advisor.” These advisors walked criminals through ransom negotiations, helped calculate what victims could realistically pay, and even drafted “proof of data deletion” statements designed to appear professional. The goal was to standardize extortion by giving low-skill affiliates the same tools and guidance as seasoned negotiators. It blurred the line between organized cybercrime and corporate customer support.
This level of professionalization sets a new precedent for ransomware-as-a-service and signals how far the underground economy has matured.
Why they made the list: Ruthless targeting of healthcare, the first ransomware “Call Lawyer” feature that professionalized extortion negotiations, rapid zero-day adoption, and coordination with state-linked operators such as North Korea’s Moonstone Sleet APT group.
Akira – The Strategic Survivor

Akira held its place near the top of the ransomware landscape in 2025, but with a clear shift in business philosophy. After earning notoriety in 2024 for devastating healthcare and education attacks, the group appeared to learn that chaos in those sectors is bad for business. Targeting hospitals brought global condemnation, government pressure, and unwanted law enforcement attention. So in 2025, Akira changed course, focusing instead on high-value enterprises and managed service providers that could pay large ransoms without triggering international outrage.
The pivot worked. Akira claimed nearly one in five global ransomware incidents this year, becoming the most consistent and financially successful operation of 2025. Their refined playbook and reputation for stability attracted skilled affiliates looking for predictable payouts.
Midyear, the group launched a concentrated wave of attacks exploiting a SonicWall SSL VPN vulnerability. The campaign affected more than 40 organizations across North America and Europe, with attackers moving from initial access to full domain compromise in under 48 hours. The operation is estimated to have generated over 40 million dollars in confirmed ransom payments by early fall.
What sets Akira apart is not only their technical precision but the way they run their enterprise. Affiliates operate under strict guidelines, ransom negotiations are conducted professionally, and even customer-style support is provided to maintain a sense of “reliability.” Some victims reported discount offers for early payment, demonstrating a transactional mindset more common to corporate sales than organized crime.
Akira has evolved from reckless disruptor to disciplined enterprise, showing that restraint and strategy can be just as dangerous as brute force.
Why they made the list: Transitioned from healthcare menace to a calculated, profit-driven operation targeting enterprises and MSPs, mastered VPN exploitation, and maintained global dominance through a tightly managed ransomware-as-a-service model.
Scattered Spider (UNC3944) – The Master Manipulators

Scattered Spider proved once again that the most dangerous exploits start with a phone call. Composed mainly of English-speaking teens and young adults, the group weaponized social engineering, SIM swapping, and deepfake voice impersonation to infiltrate major enterprises. Their campaigns against retail, insurance, and aviation companies throughout 2025 showed how psychological manipulation can defeat even advanced identity systems.
Law enforcement finally turned the tables in September. Coordinated arrests in the United Kingdom, Spain, and the United States dismantled the group’s core and seized millions in cryptocurrency. Yet the real spectacle unfolded afterward on Telegram. Within days of the takedown, a group calling itself “Scattered LAPSUS$ Hunters 4.0” began posting a series of emotional apologies. Members promised to delete stolen data, renounce ransomware, and even “use our skills for the good of this world.” One claimed they were checking into rehab for sixty days. Another signed off with a sad-face emoji.
The posts felt half confession, half performance art, revealing just how young and unpolished many of the operators were. The same hackers who once crippled casinos and retailers were now posting public, emoji-filled apologies to the very organizations they once attacked. Whether sincere or sarcastic, the spectacle underscored both the immaturity of the group and the pressure applied by international law enforcement.
Even with core members in custody, Scattered Spider’s influence persists through copycats and splinter crews. Investigators continue to track phishing domains and voice-based lures that follow the same playbook. Their mix of social engineering, arrogance, and innovation turned identity fraud into a billion-dollar weapon.
Why they made the list: Perfected deepfake voice calls and help-desk impersonation, triggered one of the most publicized law enforcement takedowns of the year, and achieved near-legendary status as access brokers whose techniques still fuel copycat groups today.
Play Ransomware – The Supply Chain Specialist

Play Ransomware quietly became one of the most destructive forces of 2025, with the FBI confirming more than 900 victim organizations. Instead of chasing headlines, Play targeted managed service providers and IT firms, exploiting remote management tools to infiltrate dozens or even hundreds of downstream clients at once. Most activity centered on North America and Europe, but attacks were also reported in Latin America and Southeast Asia as affiliates expanded their reach.
The group’s hallmark is intermittent encryption, a technique that scrambles only portions of each file. This approach speeds up deployment and reduces detection chances while still rendering data unusable. Play also favors custom-built binaries per victim, making signature-based detection nearly impossible. Their toolkit evolved through 2025 to include Linux and ESXi encryptors optimized for virtualized environments.
Victims frequently described Play’s negotiation style as calm and businesslike, complete with structured payment deadlines and threats of regulatory exposure for delay. By leveraging MSP networks and RMM platforms, Play turned every compromise into a cascading event that rippled through dependent organizations. One breach could disrupt an entire ecosystem of small and midsized businesses, earning Play its reputation as the ultimate supply chain amplifier.
Why they made the list: Precision attacks against service providers, efficient encryption methods, and unparalleled scale in supply chain exploitation.
ShinyHunters – The Silent Extortionists

ShinyHunters has mastered patience. The group infiltrates enterprise cloud platforms, stays undetected for months, and only reveals itself once entire databases are stolen and monetized. Their 2025 campaigns hit some of the world’s most recognizable brands, including Google, Salesforce, and luxury conglomerate Kering, the parent company of Gucci and Balenciaga.
The group’s breaches also highlighted the growing intersection between cybercrime and regulation. Many victims in Europe fell under GDPR disclosure requirements, and ShinyHunters learned to weaponize that process. By delaying extortion for months, they timed public leaks to coincide with or follow official regulatory notifications, maximizing embarrassment and compliance risk. The tactic turned the threat of legal scrutiny into a form of leverage all its own.
In September, ShinyHunters launched a dedicated leak site to auction stolen data, complete with tiered pricing, countdown timers, and proof-of-compromise samples. Even after several arrests in France disrupted portions of the operation, affiliates continued to run extortion campaigns independently.
Their “delayed detonation” model maximizes psychological pressure. Victims often discover breaches long after the theft has occurred, uncertain about what data was taken or when it might appear online. That uncertainty drives payments more effectively than encryption ever could.
Why they made the list: Long-term infiltration of SaaS and cloud platforms, high-profile targeting of global enterprises, and an evolved extortion model that turns regulatory pressure and brand reputation into weapons.
Lumma Stealer – The Resilient Enabler

Lumma Stealer sits at the foundation of the modern cybercrime economy. While ransomware groups dominate headlines, Lumma operates behind the scenes, quietly fueling their success by supplying the credentials and session tokens that make initial access possible. Its operators function less like hackers and more like wholesalers in a thriving underground market.
The malware’s resilience became evident in mid-2025 when a coordinated Microsoft-led takedown seized thousands of Lumma-linked domains. Within days, the group rebuilt its infrastructure and resumed operations with upgraded obfuscation and evasion techniques. The quick recovery showed that Lumma is no longer a single campaign but a living ecosystem sustained by affiliates, brokers, and developers.
We observed a surge in Lumma activity throughout 2025, with widespread infections harvesting credentials, cookies, and authentication tokens from compromised systems. These stolen credentials quickly circulated through dark web markets, where ransomware groups such as Akira, Qilin, and Play purchased them to gain direct network access. In effect, Lumma turned everyday malware infections into launchpads for multimillion-dollar ransomware events.
Lumma’s delivery methods have also evolved. One of the most concerning trends is its partnership with social engineering campaigns that use ClickFix-style lures, including fake CAPTCHA or error messages that trick users into pasting malicious PowerShell commands. This hybrid approach combines technical compromise with human deception, making traditional endpoint defenses far less effective.
Its adaptability and deep ties to criminal markets keep it at the core of today’s ransomware ecosystem. Even well-secured environments can find themselves compromised if a single employee’s credentials end up in Lumma’s collection pipeline.
Why they made the list: Acts as the backbone of modern ransomware operations, enabling access for major threat groups through massive credential theft and integration with social engineering tactics like ClickFix.
Honorable Mentions

Not every threat made the Top 6, but a few names and trends shaped how 2025 unfolded. These standouts show how fast the cybercrime ecosystem continues to adapt, evolve, and recycle ideas that never truly die. 💀
LockBit 5.0 – The Attempted Revival
LockBit spent 2025 trying to rebuild after its catastrophic takedown the year before. The new variant, LockBit 5.0, introduced faster encryption, stronger obfuscation, and cross-platform targeting for Windows, Linux, and ESXi. Despite these upgrades, the comeback has been muted. Victim counts remain far lower than at the group’s peak, and an embarrassing hack of its own admin panel in May exposed private chats and payment logs.
LockBit has since experimented with alliances, including collaborations with groups such as Qilin and DragonForce, in an attempt to restore relevance. While the technical improvements are real, the brand’s reputation remains fractured, and affiliate trust is difficult to rebuild.
Why it matters: LockBit 5.0 proves that technical upgrades cannot repair broken credibility. The group is still active but no longer dominates the ransomware landscape it once ruled.
AsyncRAT – The Remote Access Workhorse
AsyncRAT continued to spread quietly throughout 2025, powering thousands of intrusion campaigns for both low-level criminals and organized groups. Distributed through trojanized software installers and compromised IT management tools, the malware allows attackers full remote control of victim systems, including keylogging, data theft, and persistence.
Its open-source nature makes it highly customizable, spawning countless variants that slip past traditional defenses. Many ransomware groups use AsyncRAT for reconnaissance or secondary access long before deploying encryption payloads.
Why it matters: AsyncRAT remains one of the most common and versatile remote access tools on the internet, proving that open-source malware continues to blur the line between legitimate software and criminal infrastructure.
Infostealer Epidemic
Credential theft is the quiet epidemic of 2025. Infostealers such as Lumma, StealC, and Vidar have flooded underground markets with massive volumes of stolen credentials, cookies, and authentication tokens. These tools are small, fast, and cheap, making them the primary entry point for modern compromises.
The post-RedLine landscape spawned dozens of competitors that harvest browser-stored passwords, crypto wallet seeds, and 2FA tokens. Collected credentials are packaged into searchable logs and traded on Telegram channels and dark web marketplaces. That supply chain turns single-device infections into verified access listings that ransomware affiliates can buy and exploit.
Major ransomware operations rely on this pipeline. Lumma in particular serves as the core feeder, and credentials harvested by infostealers are commonly used by Akira, Qilin, and Play to obtain initial access. In short, infostealers supply the raw material that feeds ransomware, fraud, and espionage campaigns.
Why it matters: Infostealers have become the foundation of modern cybercrime, lowering the skill barrier and making rapid, large-scale intrusions possible.
ClickFix – The New Face of Social Engineering
ClickFix turned copy and paste into a weapon. Attackers use fake CAPTCHAs and error pages to trick victims into pasting commands that execute PowerShell, install stealers, or drop remote access tools. The technique bypasses email filters and many endpoint protections because the user willingly runs the command.
ClickFix became rapidly commodified via page generators that let criminals spin up convincing lures in minutes. This made it a favorite delivery method for infostealers like Lumma and for RATs such as AsyncRAT, and it was adopted by both criminal groups and advanced persistent threat actors.
Why it matters: ClickFix replaces some traditional phishing paths with a human-driven execution vector that is hard to detect with signature-based tools.
Ghastly Trends Shaping 2025
Cybercrime in 2025 has evolved into full automation. Attackers now rely on speed, deception, and AI to move from access to extortion in record time.
-
AI and Identity Collide
Deepfake voices, cloned identities, and AI-written phishing emails have made scams almost impossible to spot. Attackers now go straight for identity systems, using stolen credentials and convincing impersonations to bypass traditional defenses. -
Lightning-Speed Attack Timelines
Lateral movement that once took hours now happens in seconds. Automation and credential reuse give defenders only moments to detect and contain intrusions. -
Clipboard-Based Attacks on the Rise
Fake CAPTCHAs and error pages convince users to paste malicious commands that run PowerShell or install malware. These human-driven compromises are harder to detect than traditional phishing. -
Third-Wave Extortion Tactics
Ransomware gangs now mix harassment, DDoS, and fake regulatory complaints into their playbooks. The goal is psychological pressure rather than technical disruption. -
Data Extortion Over Encryption
Many groups skip encryption entirely, focusing on stealing and leaking data for profit. ShinyHunters and similar crews prove that data is the most valuable hostage. -
Ransom Payment Spike
Average ransom payments more than doubled this year, driven by tighter deadlines, faster breaches, and growing recovery costs. -
Malware-as-a-Service Explosion
Subscription-based platforms like Lumma, StealC, and AsyncRAT have erased technical barriers, letting anyone run professional-grade attacks. -
State-Criminal Collaboration
Groups such as Qilin blur the line between criminal and nation-state activity, merging financial motives with espionage.
Survival Tips for a Haunted Threat Landscape
Every major threat in 2025 shares one constant: speed. Once attackers gain access, automation takes over, and defenders have only moments to react.
1. Assume Compromise
Plan as if the attacker is already inside. Build defense in depth, limit privileges, and monitor internal movement. Zero trust isn’t just a buzzword anymore — it’s survival strategy.
2. Patch or Perish
Because it does. Many of this year’s top attacks started from old vulnerabilities. Prioritize known exploited flaws, especially VPN appliances, RMM tools, and email gateways.
3. Protect Identity First
Stolen credentials are now the weapon of choice. Use phishing-resistant MFA, disable legacy authentication, and rotate passwords regularly. Add user behavior analytics to detect abnormal logins.
4. Backups That Actually Work
Follow the 3-2-1-1 rule: three copies, two media types, one offsite, one offline. Test restorations often. Backups only matter if they recover cleanly when you need them most.
5. Monitor for Infostealers
Deploy endpoint detection that specifically flags browser data access, credential harvesting, and suspicious PowerShell. Even one compromised workstation can feed dozens of ransomware attacks downstream.
6. Train for the Human Factor
Run realistic phishing and voice-scam simulations. Teach employees to question unexpected pop-ups, urgent requests, and any instruction to copy and paste commands. Awareness training only works when it mirrors real attack tactics.
7. Secure Your Tools
Lock down remote monitoring and management platforms, screen-sharing tools, and cloud dashboards. Attackers love hijacking the same systems admins use to defend the network.
8. Plan Your Response
Have a documented playbook, tested communication plan, and legal contacts ready before you need them. Minutes matter when attackers automate destruction.
9. Build a Relationship with Law Enforcement
Groups like LockBit and Scattered Spider fell because of coordinated takedowns. Sharing indicators and cooperating early multiplies defense across the ecosystem.
10. Keep Learning
Threats evolve daily. Subscribe to trusted threat feeds, follow your vendor advisories, and stay engaged in cybersecurity communities. Awareness is still the most affordable defense.
Download the infographic below!







