by Brian Donohue/ Posted on 10/17/2014
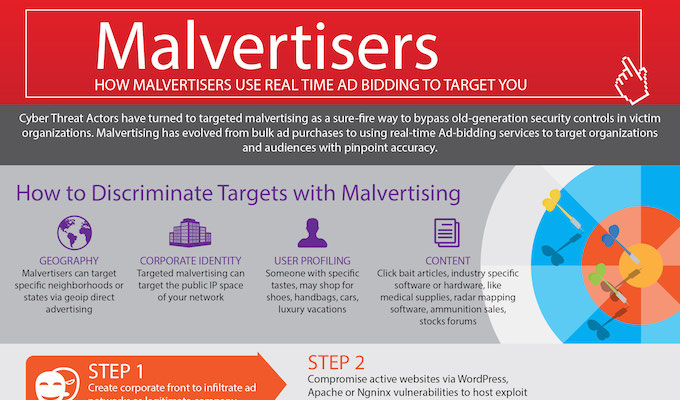
Advanced persistent threat groups are using malvertising in order to compromise the networks of their adversaries in what appears to be an example of high-level, nation-state attackers borrowing tactics from the typically less sophisticated cybercriminal arsenals. Attackers are also borrowing from the corporate marketing world by leveraging a form of high-speed advertisement placement known as “real-time ad-bidding.” In a report made public today, the Virginia-based security firm Invincea says it has discovered a state-sponsored APT campaign, dubbed “Operation DeathClick.” They claim that they blocked the attacks and were therefore not able to determine much in the way of attribution, but the attack itself is novel in the way it deployed a new and aggressive form of malvertising. Invincea claims this isn’t your standard, criminal variety of malvertising. Traditional malvertising is indiscriminate. Criminals compromise an online advertising network and use the network’s ads to redirect as many users as possible to third party sites containing exploit kits and malware. In certain greyer cases the ad networks act unscrupulously themselves.
Full Article
APTs Target Victims with Precision, Ephemeral Malvertising
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.