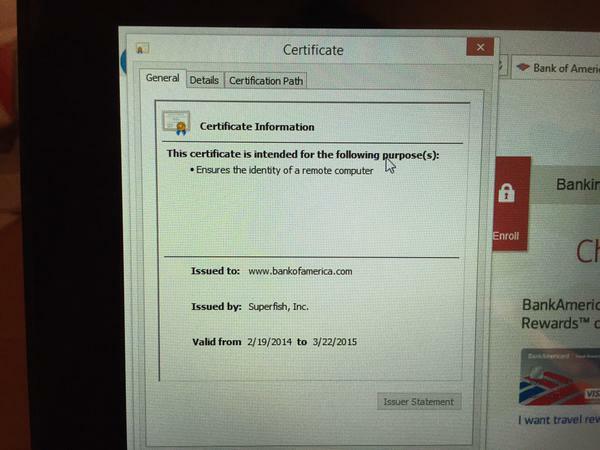
Lenovo Accused of Shipping PCs With Adware That Breaks HTTPS Browsing
By Eduard Kovacs on February 19, 2015 Many Lenovo users started complaining last year about a piece of adware being pre-installed on their new computers. After a close analysis, experts have determined that the application poses serious security risks. The culprit appears to be WindowShopper - Discover Visually, a browser add-on developed by visual search company Superfish. The application analyzes images displayed on Web pages and searches for similar or nearly identical items so that users can compare prices and find deals. The add-on basically injects third-party ads into Web pages. Full Article
Reply
Login to the community
No account yet? Create an account
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.