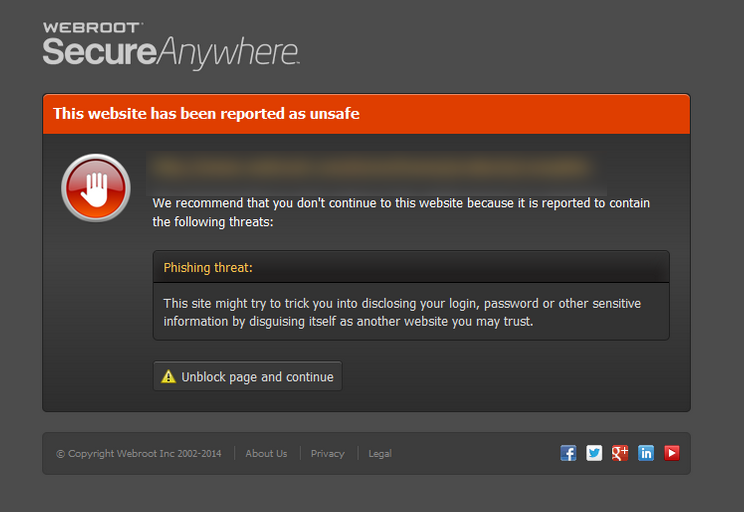
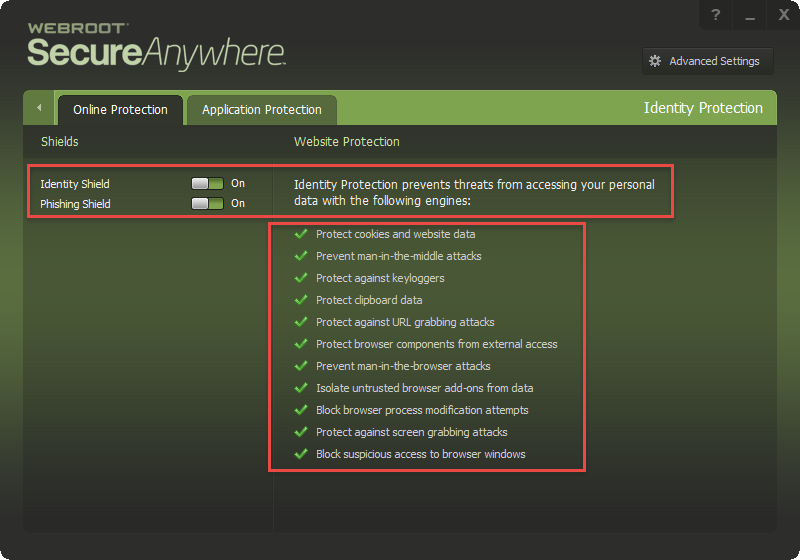
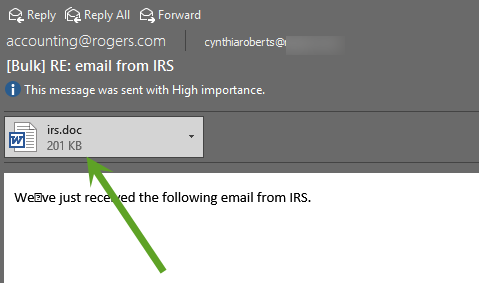
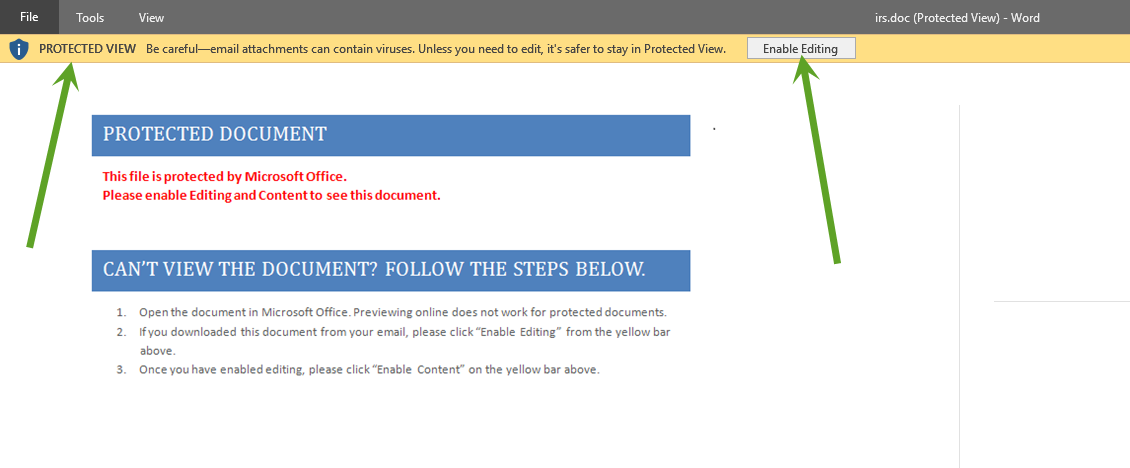
How to be prepared for a browser-based attack
http://images.techhive.com/images/article/2015/11/tripbox-malvertising-2-100627715-primary.idge.jpg
How a large video malvertising campaign attacked users according to The Media Trust.
Credit: The Media Trust
When a catastrophic attack hits, companies either have to start over or pay the ransom, as we've seen far too often in the headlines.
"One of the first things anybody needs to do is create a backup of their system. They need a backup system for long term storage of the data that they love," said Invincea’s director of security analytics, Pat Belcher. "You’d be surprised at how many veterans ignore this as well."
Belcher offered an overview of what Invincea has identified as the most advanced endpoint threat trends of browser-based attacks along with some suggestions for prevention, detection, and response.
Full Article