January 15, 2020 By Tony Kueh
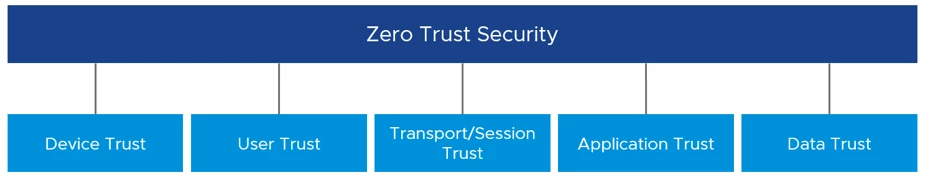
There are five different pillars to implement when moving to a modern, zero-trust security model.
Employees are demanding that employers enable flexible workstyles. Apps are moving to the cloud. A company’s device and application mix are increasingly heterogeneous. All of these factors are breaking down the enterprise security perimeter, rendering traditional security approaches obsolete, and paving the way for zero-trust approaches.
Traditional security methods broadly classify everything (users, devices and applications) inside the corporate network as trustworthy. These models leverage legacy technologies, such as virtual private networks (VPNs) and network access control (NAC), to verify the credentials of users outside the network before granting access. The focus therefore is on strengthening the network perimeter and then granting full access to corporate data once credentials are successfully validated. This is sometimes referred to as the “castle and moat” approach, in which the castle refers to the enterprise holding valuable data and applications, while the moat refers to layers of protection aiming to keep potential threats out.