May 13, 2024 By Bill Toulas
Threat actors are using Domain Name System (DNS) tunneling to track when their targets open phishing emails and click on malicious links, and to scan networks for potential vulnerabilities.
DNS tunneling is the encoding of data or commands that are sent and retrieved via DNS queries, essentially turning DNS, a fundamental network communication component, into a covert communications channel.
The threat actors encode the data in various ways, such as Base16 or Base64 or custom textual encoding algorithms, so they can be returned when querying DNS records, such as TXT, MX, CNAME, and Address records.
Hackers commonly use DNS tunneling to bypass network firewalls and filters, employing the technique for command and control (C2) and Virtual Private Network (VPN) operations. There are also legitimate DNS tunneling applications, such as for bypassing censorship.
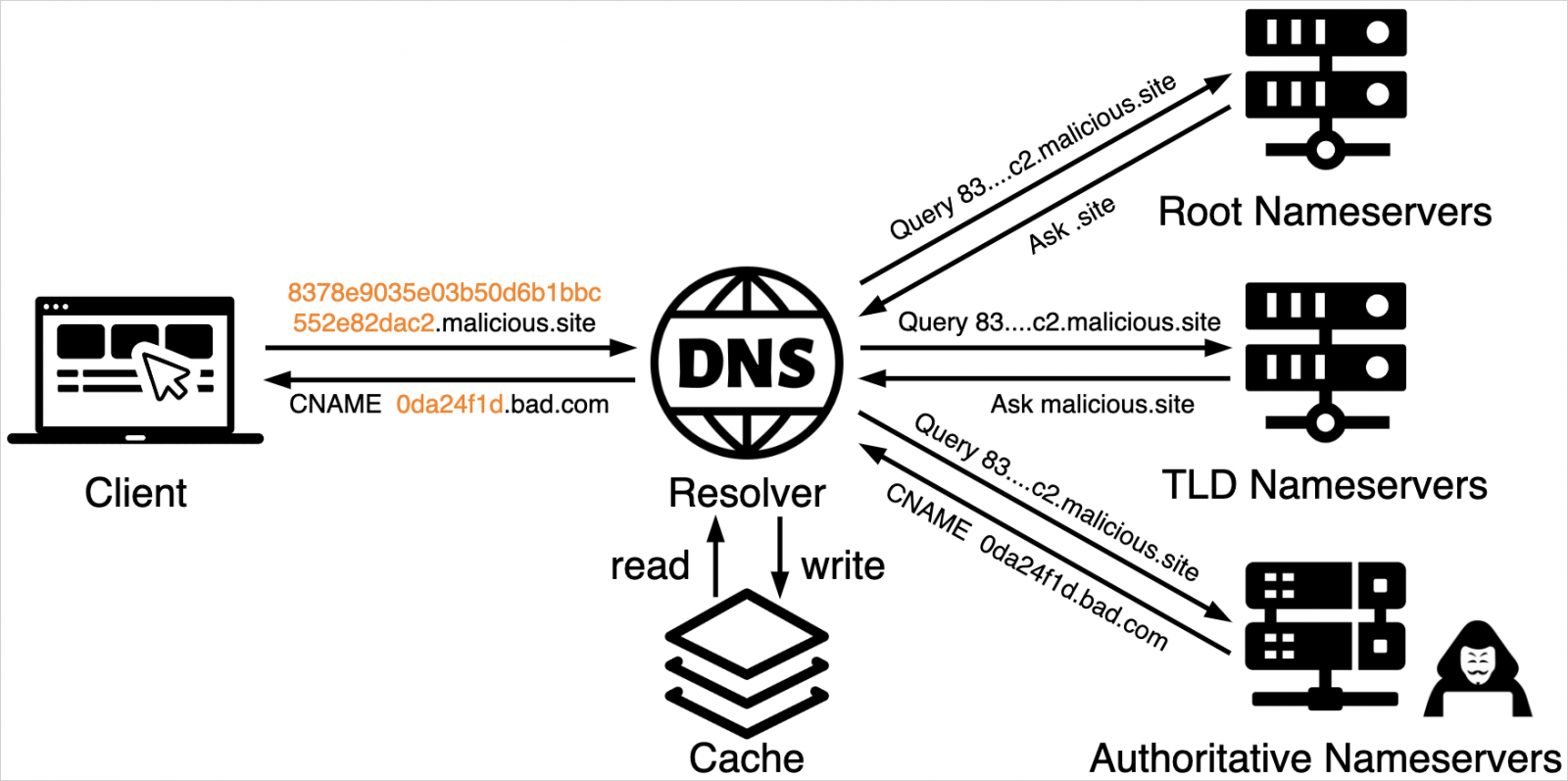
Source: Unit 42
Palo Alto Networks' Unit 42 security research team recently discovered additional use of DNS tunneling in malicious campaigns involving victim tracking and network scanning.


