October 30, 2025
Categories:
Cyber Security News Cybersecurity Vulnerability
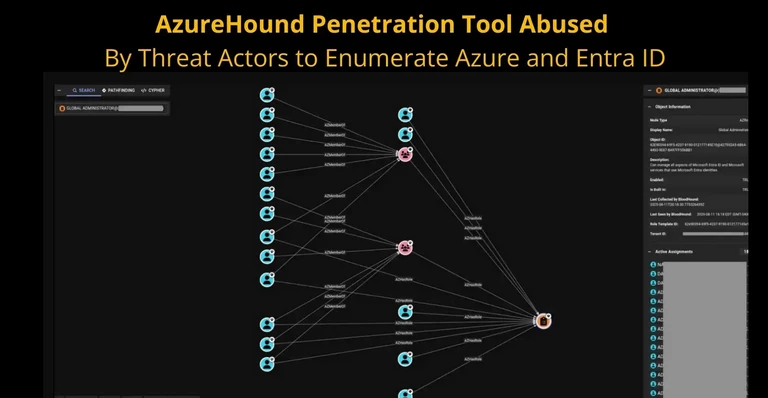
The cybersecurity landscape continues to shift toward cloud-based attacks, with threat actors increasingly exploiting legitimate security tools for malicious reconnaissance.
AzureHound, a penetration testing utility designed for authorized security professionals, has become a weapon of choice for attackers seeking to understand and compromise Azure and Microsoft Entra ID environments.
Security researchers have documented sophisticated adversaries using this tool as part of coordinated post-compromise activities, fundamentally changing how defenders must approach cloud security monitoring.
Understanding the Weaponization Threat
AzureHound is a data collection tool built into the BloodHound suite, created to help defenders identify vulnerabilities in cloud infrastructure.
The tool functions by querying Microsoft Graph and Azure REST APIs to gather detailed information about users, groups, permissions, roles, and resources.
However, threat actors have weaponized this legitimate software to accelerate their attack timelines and operate efficiently within victim environments.
Recent threat intelligence reveals that sophisticated adversaries, including Iranian-backed Curious Serpens and Russian-affiliated Void Blizzard, have incorporated AzureHound into their post-compromise discovery phases.


