Yesterday, a Cloudflare service disruption caused widespread accessibility issues across major websites. While this was not a cyberattack, the incident exposed how heavily the modern internet depends on a small number of infrastructure providers. Cloudflare acts as the front door for a massive portion of the web. When it blinks, the entire ecosystem feels it. Even Downdetector struggled to load, leading to the bizarre moment where users tried to access “is Downdetectordown.com” and found that down as well.
What Actually Happened
Cloudflare experienced a temporary outage that affected multiple services including CDN routing, DDoS protection layers, and access control checks. Early indicators suggest the disruption originated from a failure in Cloudflare’s challenge and verification systems, particularly around challenges.cloudflare.com, which handles bot mitigation and client validation.
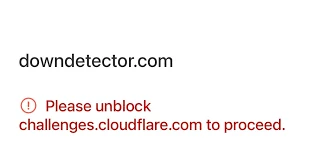
Users saw errors such as:
-
“Please unblock challenges.cloudflare.com to proceed”
-
Timeouts when sites tried to load Cloudflare challenge scripts
-
Repeated verification loops
When Cloudflare’s challenge service fails, legitimate traffic can be incorrectly blocked or stalled, which creates the perception that the website itself is down even if the host servers are operational.
This explains why unrelated sites that rely on Cloudflare suddenly became unreachable.
Why Even Downdetector Broke
This was one of the most ironic parts of the morning. Downdetector relies on third-party infrastructure providers for traffic routing and security filtering. When Cloudflare’s verification endpoint malfunctioned, Downdetector pages failed to load.
Users went to sites like “is Cloudflare down” and saw errors. Then they went to “is Downdetector down” websites and found those pages down too. It created a loop where even the tools designed to tell you something is down were also down.
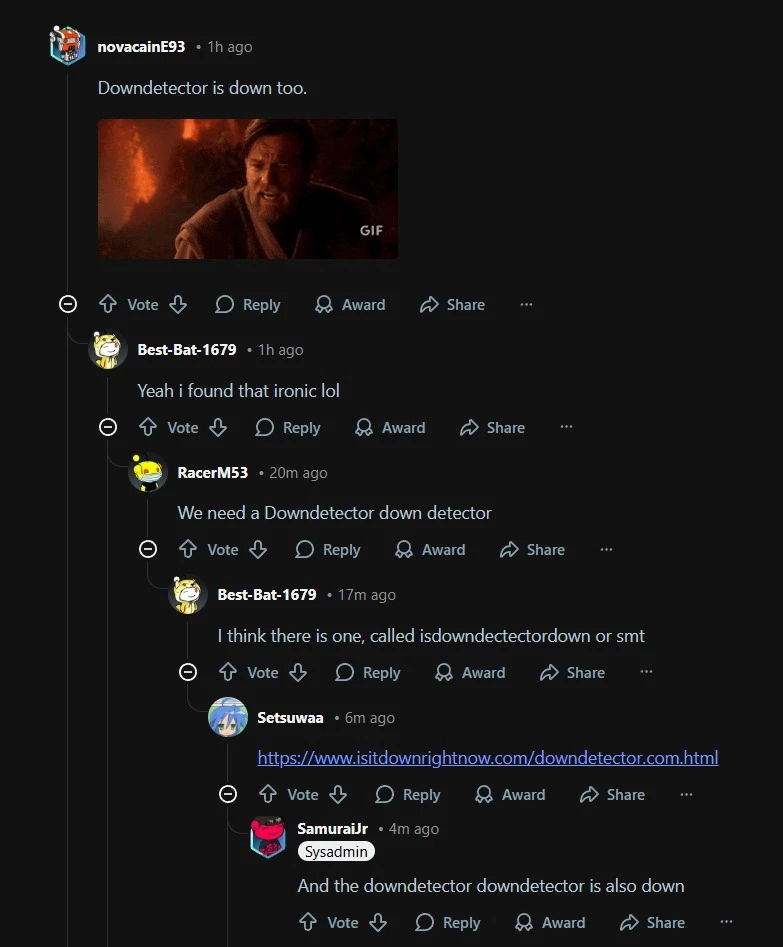
This was not the result of any threat activity. It was simply the internet’s dependency on a few critical layers all failing at once.
Full Forensics Style Breakdown
Root cause
A Cloudflare-side issue in the traffic challenge layer. The challenge service is used by thousands of websites to block bots, verify real users, and enforce security policies. When this component experienced errors, traffic validation failed at scale.
Impact
-
Websites protected by Cloudflare became inaccessible or repeatedly reloaded
-
API calls dependent on Cloudflare edge routing failed
-
Downdetector and similar “site status” services experienced failures at the same time
-
Third-party monitoring tools that rely on Cloudflare’s CDN or DNS also misreported site status
-
Widespread perception of total outages for major brands
What it was NOT
-
Not a DDoS attack
-
Not a breach
-
Not a ransomware event
-
Not targeted activity against critical infrastructure
Why it looked like an attack
Simultaneous failures across multiple unrelated sites trigger the same widespread symptoms we associate with coordinated threat campaigns. In reality, the internet’s shared infrastructure created a cascading effect.
The Bigger Conversation: Internet Fragility
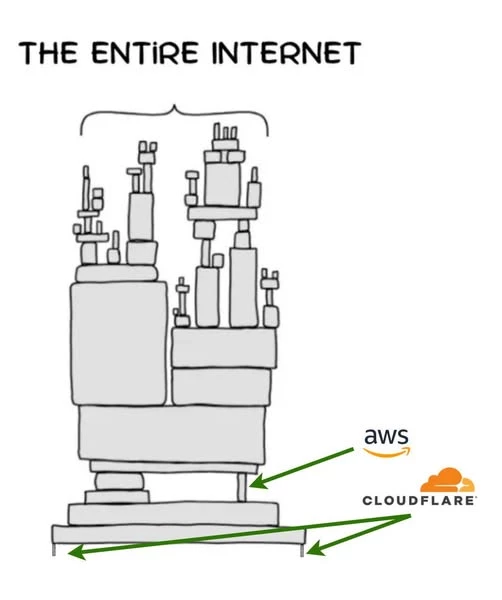
The incident highlights a growing systemic risk. The modern internet relies heavily on three giants:
-
Google Cloud
-
Amazon Web Services
-
Cloudflare
Between them, they support a massive portion of the global internet. A problem in any one of these layers can ripple outward and degrade thousands of services simultaneously.
This is similar to the concept of a single point of failure in network design. Except now that point of failure sits at the global provider level.
Today showed how even a short disruption at a single provider can create:
-
False outage reports
-
Broken authentication flows
-
Delayed API responses
-
Load balancer failures
-
Global confusion on social platforms
-
And even outages in the tools that detect outages
It was a reminder that the internet is huge but its foundation is surprisingly centralized.
Key Takeaways for SMBs and Enterprises
-
Do not assume a website outage is always a cyberattack
-
Service providers should review their dependency chains
-
Redundancy planning should include CDN and DNS layers
-
Organizations should consider multi-CDN or multi-cloud strategies
-
Monitoring tools should be diversified so they are not impacted by the same outage
Cloudflare restored functionality quickly, and there is no evidence of malicious activity. But the outage serves as a real-world demonstration of how fragile the global internet can be when so much traffic is funneled through a handful of companies.
It is rare to see a disruption so widespread that even Downdetector cannot report the outage. The fact that users had to rely on screenshots and social media memes to confirm Cloudflare was down says everything.
If you want, I can attach your two images to this post and create an HTML or Markdown version for your community portal.





