September 4, 2025 By Mirko Zorz
Today at Nullcon Berlin, a researcher disclosed a macOS vulnerability (CVE-2025-24204) that allowed attackers to read the memory of any process, even with System Integrity Protection (SIP) enabled.
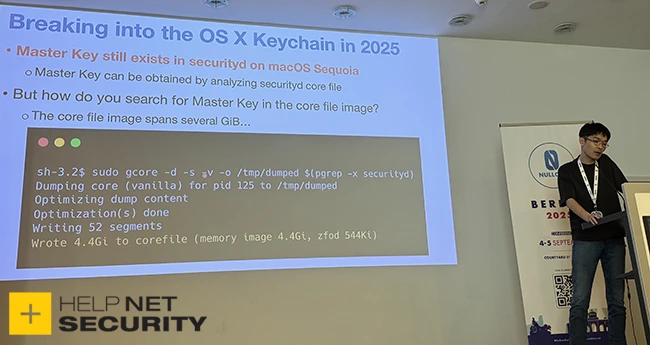
The issue stems from Apple mistakenly granting the /usr/bin/gcore utility the com.apple.system-task-ports.read entitlement in macOS 15.0 (Sequoia). Apple removed the entitlement in macOS 15.3.
Koh M. Nakagawa speaking at Nullcon Berlin 2025
This entitlement gave gcore the ability to read the memory of any process on the system. Security researcher Koh M. Nakagawa of FFRI Security discovered that this broke a key security boundary and exposed sensitive user data, including contents of the Keychain, data protected by Transparency, Consent, and Control (TCC), and even encrypted iOS app binaries.




