February 11, 2025 By Bill Toulas
Over twelve thousand GFI KerioControl firewall instances are exposed to a critical remote code execution vulnerability tracked as CVE-2024-52875.
KerioControl is a network security suite that small and medium-sized businesses use for VPNs, bandwidth management, reporting and monitoring, traffic filtering, AV protection, and intrusion prevention.
The flaw in question was discovered in mid-December by security researcher Egidio Romano (EgiX), who demonstrated the potential for dangerous 1-click RCE attacks.
GFI Software released a security update for the problem with version 9.4.5 Patch 1 on December 19, 2024, yet three weeks later, according to Censys, over 23,800 instances remained vulnerable.
Early last month, Greynoise revealed it had detected active exploitation attempts leveraging Romano's proof-of-concept (PoC) exploit, aimed at stealing admin CSRF tokens.
Despite the warning about active exploitation, threat monitoring service The Shadowserver Foundation now reports seeing 12,229 KerioControl firewalls exposed to attacks leveraging CVE-2024-52875.
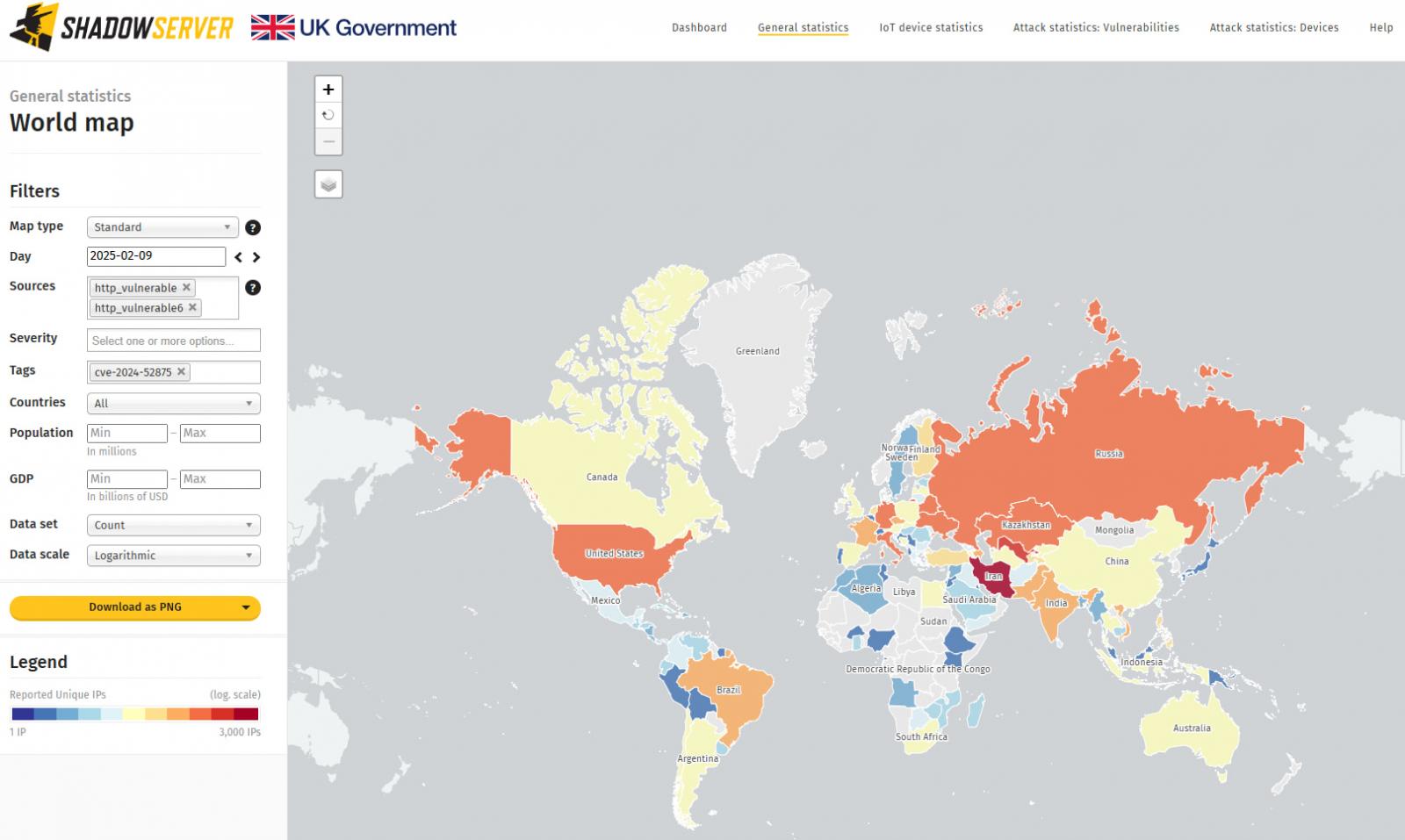
Source: The Shadowserver Foundation


