Our favorite Sr. Threat Researcher,
General News
Booter Boss Banged Up for 13 Months
DDoS attacks can be used for many malicious purposes. Whether it’s bringing down major British political party websites or cheating at online games, DDoS attacks have been making headlines recently. The arrest and conviction of Sergiy P. Usatyuk should worry other criminals who sold DDoS for hire services. As is often the case in the cybercrime sphere, justice hasn’t been swift and the charges related to events in August 2015 to November 2017 where Usatyuk is said to have earned a little over half a million US dollars.
More: Infosecurity Magazine
Webroot Part of Top Ten in Windows Anti-Malware Market Share
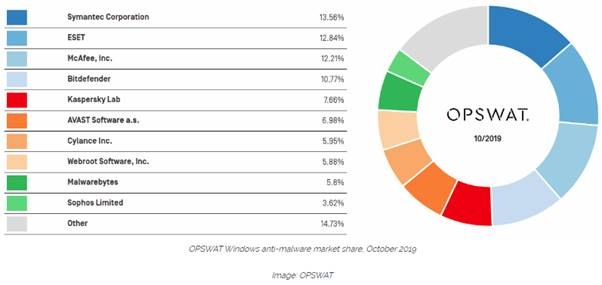
More: ZD Net
Cryptocurrency
Coin Stealer Found in Monero Linux Binaries from Official Site
Monero is one of the most popular cryptocurrencies in the world.
It’s website “getmonero.org” was compromised and coin stealing malware was put up on the site which has been seen stealing coins from victims. As far as hacks go this is brazen and very effective. Monero to their credit, seem to have reacted fast to the breach and have cleaned up the site and their binaries as well as issuing a warning to users.
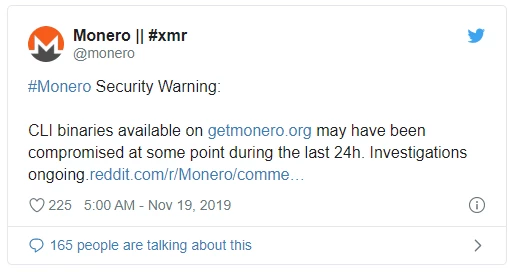
“Yesterday a GitHub issue about mismatching hashes coming from this website was opened. A quick investigation found that the binaries of the CLI wallet had been compromised and a malicious version was being served. The problem was immediately fixed, which means the compromised files were online for a very short amount of time. The binaries are now served from another, safe, source. See the reddit post by core team member binaryfate.
It's strongly recommended to anyone who downloaded the CLI wallet from this website between Monday 18th 2:30 AM UTC and 4:30 PM UTC, to check the hashes of their binaries. If they don't match the official ones, delete the files and download them again. Do not run the compromised binaries for any reason.”
~Monero
More: Bleeping Computer
Over Two Million Gamers and Crypto Wallet Users Hit in Breaches
“Over two millions users of a gaming company and a cryptocurrency specialist have become the latest "netizens" to have their personal data compromised by attackers.
The haul includes 1.4 million accounts from users of cryptocurrency wallet service GateHub, which were posted to a popular hacking forum, according to the breach notification site HaveIBeenPwned?”
More: Infosecurity Magazine
Ransomware
French Hospital Crippled by Ransomware
The health sector is a tempting target for cyberattacks and is especially vulnerable to ransomware. Hôpital Charles-Nicolle De Rouen has over 1300 beds and 8000 staff and the attack has caused major disruption to staff and patients alike.
More: Infosecurity Magazine
400 Vet Locations Nipped by Ryuk Ransomware
Based in California, the National Vetinary Association caters for 400 clinics across the USA. The attack affected a large number of machines at the NVA and patchy reports suggest serious disruption. The head of tech at the affected company has claimed that this is the result of a supply side attack which suggests that it was pre-meditated and targeted.
More: Threatpost
New NextCry Ransomware Encrypts Data on NextCloud Linux Servers
Ransomware usually entails encrypting data on Windows machines or their share drives. The criminal practice of encrypting valuable data before demanding a ransom is seen elsewhere, however. Nextcloud is a file sync and share service that has seen some weaknesses in its security and default configuration exploited by a new ransomware campaign. The malicious encryption affects the cloud copies of a victim’s files and since the local copies they have are synced (read replaced) by the encrypted versions they risk losing their backup and original copies.
More: Bleeping Computer
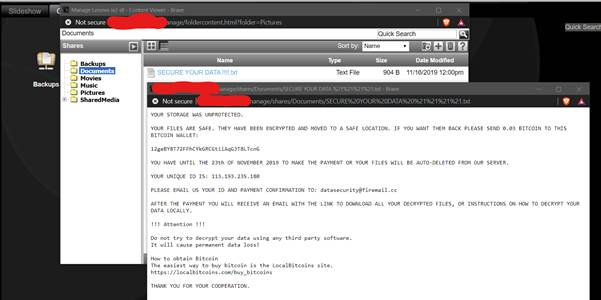
Unsecured Lenovo "Iomega" Devices on Shodan Are Being Ransomed En Masse
Lenovo Iomega devices connect directly to the internet meaning that they are an easy file storage device to setup and use. With this convenience comes risk however and vulnerabilities in the device mean that many are being encrypted and held to ransom.
More: Twitter
Buran Ransomware Infects PCs via Microsoft Excel Web Queries
Louisiana State Government Hit by Ransomware Attack Forcing Server Shutdowns
Louisiana State is just another government target in a long list of targets on US governance. It truly is an epidemic and other states affected by similar attacks include Texas, Virginia, North Carolina, Atlanta, Florida and New York.
More: The Hacker News
Fake Windows Update Spam Leads to Cyborg Ransomware and Its Builder | Trustwave
Cyborg ransomware is being pushed by fake Microsoft update emails. Updates are important for security and as well as causing damage in the short term, fake updates undermine the general confidence people have updating, and this leads to weaker security as a whole. The sheer number of updates that we all see on a day-to-day basis means that users are unlikely to spend much time investigating any notifications
More: SC Magazine
Hacks & Breaches
1.19 Billion Confidential Medical Images Available on The Internet - Help Net Security
Attacks on healthcare aren’t limited to ransomware and theft and leaks are also extremely common in this vulnerable industry.
More: Helpnet Security
Phoenix Keylogger Turns off AV Products Before Stealing Data
Keyloggers typically read the keys pressed on a machine so that they can steal valuable information such as credit cards numbers and credentials. They may also steal clipboard data and other information too. We haven’t been hearing much about keyloggers in recent years so the surging reports of the Phoenix keylogger is surprising. It is a technically impressive piece of malware that includes many modern banking trojan techniques. One of these techniques is switching off AV products.
More: ZD Net
Gaming Users Exposed After Wizards of The Coast Leak
“A US gaming company has admitted accidentally leaking the personal data of countless customers via a cloud storage bucket.
Hasbro-owned Wizards of the Coast specializes in fantasy and science fiction games such as card trading title Magic: The Gathering.”
More: Infosecurity Magazine
Exposed Database Left Terabyte of Travellers’ Data Open To The Public - CNET
“The exposed database contained travellers’ information like names, home addresses, lodging, children's personal information, credit card numbers and thousands of passwords stored in plaintext, the security researchers said Wednesday. The database stores information on 140,000 clients, each of which could be an individual, a group of travellers or an organization.
The database belongs to Gekko Group, a subsidiary of France-based AccorHotels, Europe's largest hospitality company. Gekko Group handles business travel and luxury travel with more than 600,000 hotels across the world, according to its website. AccorHotels referred to Gekko Group for comment.”
More: CNet
This is the first time this has ever happened. Getmonero.org has had a clean track-record of safe downloads for almost a decade. So whoever pulled this off was -incredibly- talented. Hats off to the Monero team to fixing this as fast as they did - hopefully not too many funds were lost before the fix. What do you guys think about Monero/Crypto? Are you interested in Cryptocurrency and want more news from us about this space? I’d love some discussion on these topics below - let me know what you think!

