You can deploy the SecureAnywhere installer file using one of these methods:
- Install SecureAnywhere on each endpoint.
- Send emails to end users, so they can install the software by clicking on the link provided in the email template.
- Rename the executable file using your keycode. This method is useful if you plan to use your own deployment tool and if you prefer not to use MSI commands to run the installation in the background.
- Use additional commands with the executable file to deploy it in the background.
- Use command-line options with the installer to deploy to endpoints that are behind a proxy server.
1. On the endpoint, download the SecureAnywhere installer file.
The installer file is available from the Resources tab or by clicking this link:
http://anywhere.webrootcloudav.com/zerol/wsasme.exe
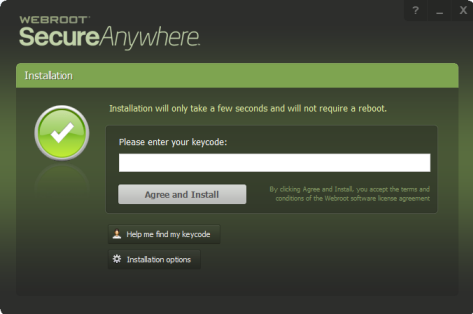
2. In the installation panel (shown below), enter the keycode.
Your keycode is shown in the Resources tab.
3. Optionally, you can click Change installation options at the bottom of the installation panel and set these options:
- Create a shortcut to SecureAnywhere on the desktop. This option places a shortcut icon on the Windows Desktop for SecureAnywhere.
- Randomize the installed filename to bypass certain infections. This option changes the Webroot installation filename to a random name (for example, “QrXC251G.exe”), which prevents malware from detecting and blocking Webroot’s installation file.
- Protect the SecureAnywhere files, processes, and memory from modification. This option enables self-protection and the CAPTCHA prompts. (CAPTCHA requires you to read distorted text on the screen and enter the text in a field before performing any critical actions.)
- Change Language. To change the language displayed in SecureAnywhere, click the Change Language button and select from the supported languages. (You can only change the displayed language during installation, not after.)
During installation, SecureAnywhere runs an immediate scan on the endpoint.
To run a background installation from a command line:
1. On the endpoint, download the SecureAnywhere installer file:
http://anywhere.webrootcloudav.com/zerol/wsasme.exe
2. Run the installer from a command line, using any of the command options listed in the following table. More options are available; for more information, contact Webroot Business Support.
Command Lines for Windows
Command LineDescription
/key=keycodeInstalls with the provided keycode, with or without hyphens.
For example:
wsasme.exe/key=xxxx-xxxx-xxxx-xxxx-xxxx
/silentInstalls in the background.
/nostartInstalls without starting SecureAnywhere.
/lockautouninstall=passwordCorresponds to /lockautouninstall. Example: wsasme.exe/autouninstall=password
By default, SecureAnywhere does not display in the Add/Remove Programs list in the Control Panel, which prevents the user from removing the software in unmanaged mode.
-cloneFor cloned machines/VMs use this to have the agent create a persistent, unique value on the PC which will change what is displayed in the portal for the machine IDs and the hostname of the PC.
The product log will indicate this flag being present for the administrator to be aware of which PC they're looking at, for example "Applied unique machine ID: C8137921" where C8137921 matches the hostname, for example, PCHOSTNAME-C8137921, as well as the first 8 bytes of both the InstanceMID and DeviceMID to allow each of them to be identifiable and different than the original IDs.
This value will persist if the agent is uninstalled/reinstalled so that existing agents won't move to other IDs. If the OS is reinstalled, the ID will change.
Example:
wsasme.exe /key=xxxx-xxxx-xxxx-xxxx-xxxx /silent -clone
Note: For use when InstanceMID's are matching causing duplicates in the console or endpoints replacing endpoints at each poll interval.
-uniquedeviceTakes a checksum of the hostname and modifies the machine IDs with it. This is useful if they have machines where the OS or hardware are cloned but the hostnames are always different. In this case, the unique hostname will allow there to be unique machine IDs. The hostname remains untouched so it will be reported into the console exactly as it exists within the OS.
Typically used for virtual environments like Citrix Provisioning or VDI where the use of -clone is not effective due to Device MIDs being the same.
Example: wsasme.exe /key=xxxx-xxxx-xxxx-xxxx-xxxx /silent -uniquedevice
Note: For use when DeviceMID's are matching causing duplicates in the console or endpoints replacing endpoints at each poll interval.
/exeshowaddremoveIncludes SecureAnywhere in the Control Panel Add/Remove Programs list.
Example:
wsasme.exe /key=xxxx-xxxx-xxxx-xxxx
/lockautouninstall=password/exeshowaddremove
Note: Adding SecureAnywhere to Add/Remove Programs enables the endpoint user to remove the software in unmanaged mode.
/group=groupcodeCommand line switch for deploying directly into groups.
Example:
wsasme.exe /key=xxxxxxxxx /group=-135260017840748808 /silent
Assign endpoints to a specific group by selecting the group you want to add endpoints to, then from the Actions drop-down menu, select Deploy Endpoints to this Group. Note the GROUPCODE.
Other requirements:
- The group must already exist in the console.
- This only works new for new installs on systems that have never been seen by the console previously.
msiexec /i "C:wsasme.msi" GUILIC="XXXX-XXXX-XXXX-XXXX" CMDLINE="SME,quiet,Group=-135260017840748808" /qn /l*v %windir%wsa_install_log.txt
For MSI installs you can use command line and an MSI editor.
Example for MSI Editor in CMDLINE field:
Group=-135260017840748808
-proxyhost=X -proxyport=X -proxyuser=X -proxypass=X -proxyauth=#Specifies proxy settings.
Note: If the endpoint connects through a proxy server, SecureAnywhere will automatically detect the proxy settings. SecureAnywhere checks for changes to the proxy settings every 15 minutes and when the endpoint restarts. We recommend using auto-detection for proxy settings; however, you can use command-line options if you prefer.
To enable proxy support, use these command-line options: wsasme.exe -proxyhost=nn.nn.nn.nn -proxyauth=n (where n can be 0=Any, 1=Basic, 2=Digest, 3=Negotiate, 4=NTLM) -proxyuser=proxyuser -proxypass=password -proxyport=port_number
We recommend that you use a specific value for-proxyauth, instead of 0 (any). The any option requires the endpoint to search through all authentication types, which might result in unnecessary errors on proxy servers as well as delayed communications.
If you use this command-line option, use all parameters and blank out any value you don't need with double quotes, for example: proxypass=""
/lang=LanguageCodeSpecifies the language to use for the product, rather than allow default language detection. Codes include:
en — English
ja — Japanese
es — Spanish
fr — French
de — German
it — Italian
nl — Dutch
ko — Korean
zh-cn — Simplified Chinese
pt — Brazilian Portuguese
ru — Russian
tr — Turkish
zh-tw — Traditional Chinese
Example:
wsasme.exe /key=xxxxxxxxxxxx /silent /lang=ru