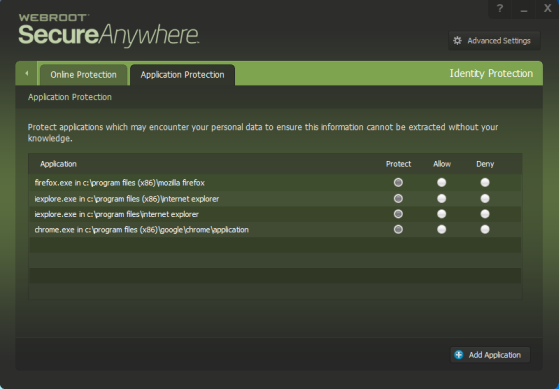
- Protect. “Protected applications” are secured against information-stealing malware, but also have full access to data on the system. You might want to add financial management software to the category. When you run a protected application, the Webroot icon in the system tray displays a padlock:
- Allow. “Allowed applications” are not secured against information-stealing malware, and also have full access to protected data on the system. Many applications unintentionally access protected screen contents or keyboard data without malicious intent when running in the background. If you trust an application that is currently marked as “Deny,” you can change it to “Allow.”
- Deny. “Denied applications” cannot view or capture protected data on the system, but can otherwise run normally.
To manage the application list and specify levels of protection:
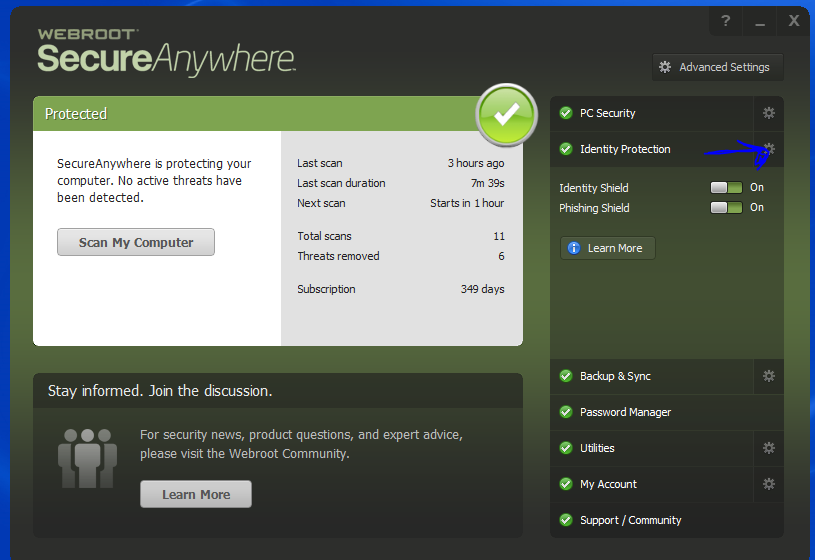
- Open SecureAnywhere (see Using the SecureAnywhere interface)
- Click the gear icon next to Identity Protection.
- Click the Application Protection tab.
- In the row for the application you want to modify, click the radio button for Protect, Allow, or Deny. The grey button indicates it is enabled; white is disabled. To include another application in this list, click Add Application, then select an executable file.